Email remains one of the most exploited channels in aviation, used by attackers for phishing, spoofing, and business email compromise (BEC) schemes. The aviation sector – from global airlines to private charter companies – is experiencing a surge in cyberattacks. In fact, cyberattacks on aviation rose by 131% between 2022 and 2023. Phishing has become especially prevalent, accounting for roughly 15.3% of all cyber incidents in aviation in recent years. These email-based threats aren’t just theoretical: they have led to costly breaches, financial fraud, and severe reputational damage in our industry.
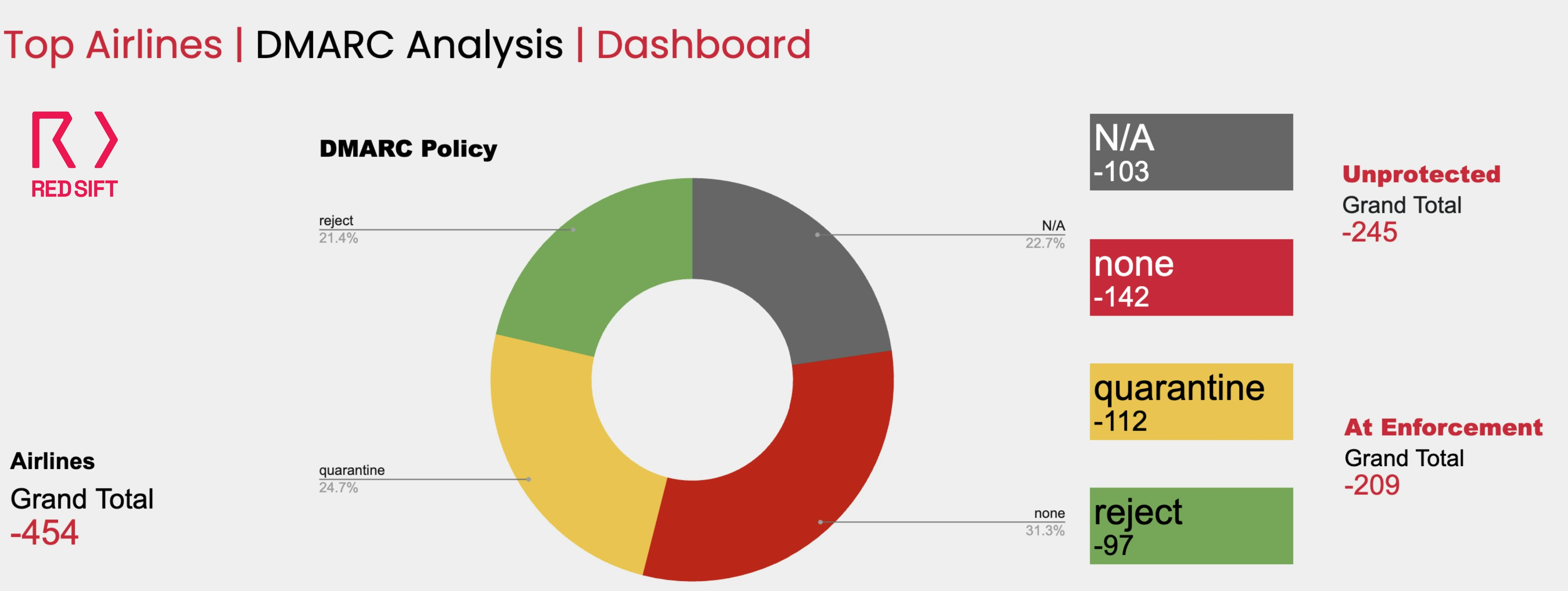
Despite this rising threat, many aviation organizations have yet to fully deploy email authentication defenses. Research by Red Sift reveals 78.6% of global airlines have not implemented “p=reject” DMARC protection (the strictest enforcement), and 22.7% of airlines lack any Domain-based Message Authentication, Reporting, and Conformance (DMARC) record at all. This leaves passengers, partners, and airlines themselves exposed to fraudulent emails. To protect the aviation sector’s critical communications and brand trust, it’s urgent to implement DMARC and reach full enforcement.

This guide will illustrate why DMARC is so vital for aviation, how it works, and the step-by-step path to achieving p=reject – along with the risks of doing nothing. We’ll also highlight real-world incidents (from multimillion-dollar scams to new “SubdoMailing” attacks) that underscore the cost of weak email security. By the end, aviation stakeholders will see the urgency of DMARC enforcement and how solutions like Red Sift OnDMARC can make implementation easier.
Phishing, BEC, and SubdoMailing attacks
Aviation is a prime target for cybercriminals. Airlines, airports, and aerospace firms handle high-value transactions and sensitive logistics, making them attractive victims for email fraud. Let’s look at the key email threats facing our industry, with data highlighting their impact:
- Phishing attacks: Phishing scams impersonate trusted senders to trick recipients into clicking malicious links or divulging credentials. In aviation, phishing is on the rise post-pandemic as travel rebounds. Recent analyses show phishing now constitutes over 15% of cyberattacks on aviation. Every day, attackers send fake ticket invoices, bogus flight cancellation notices, and other scams to airline customers – often using the airlines’ own domain names to appear legitimate.
- Business Email Compromise (BEC): BEC is a highly targeted fraud where attackers impersonate executives or trusted partners via email to trick employees into sending money or sensitive information. The aviation industry has seen dramatic BEC heists. A notorious example is the 2016 FACC incident: Fischer Advanced Composite Components (an Austrian aerospace company) lost approximately €42 million after an attacker spoofed the CEO’s email and convinced an employee to wire funds for a fake acquisition. The email impersonated the CEO, and without proper authentication checks, it looked credible – resulting in a massive transfer before the fraud was caught. This “fake CEO” scam is a classic BEC tactic, and it preyed on the lack of email authentication. Aviation and aerospace firms have also been hit by BEC schemes targeting invoice payments and supplier communications.
- SubdoMailing (subdomain-emailing) attacks: A new and sophisticated threat has emerged that specifically exploits gaps in email authentication. “SubdoMailing” is a tactic where attackers hijack unused or poorly configured subdomains of a company’s domain to send malicious emails that bypass DMARC checks. In early 2024, researchers uncovered a massive SubdoMailing phishing campaign sending up to 5 million emails per day from over 8,000 compromised domains and 13,000 subdomains.
How does it work?
If an airline or aviation company has a dangling DNS entry (say a defunct subdomain that still exists in DNS), attackers can take it over and send emails as reservations.yourairline.com or another trusted subdomain.
Because the top-level domain might have DMARC set up only for itself and not properly cover subdomains, these fake emails can pass even strict DMARC policies, appearing authentic to recipients. In short, SubdoMailing turns an organization’s own subdomains into weapons against it, exploiting DNS hygiene issues. This is an especially dangerous development for aviation, where companies often use many subdomains for different services (booking, cargo, support, etc.).
Bad actors actively exploit DNS misconfigurations to send fraudulent emails on behalf of legitimate aviation brands, proving that a DMARC policy is only as strong as the domain’s DNS configuration. The scale and stealth of SubdoMailing campaigns make them a pressing concern for any security-conscious airline or aerospace firm.
Real-world impact
The consequences of these threats are very real. Beyond the FACC financial loss, consider the reputational damage when customers receive scam emails that look like they’re from an airline. Trust is critical in aviation – passengers need confidence in communications about their bookings and safety. In one recent incident, a phishing email impersonated the CEO of FlySafair (a South African airline), complete with the company’s branding, to trick employees into clicking a malicious link. The attack leveraged a compromised email account to bypass security and nearly harvested confidential credentials.
Fake ticketing scams have also targeted airline customers, where emails that appear to come from an airline inform the recipient of a bogus booking or prize, luring them to click malware-laden attachments or links. If an airline’s domain is not protected, cybercriminals can send out these scams at scale, potentially defrauding travelers or disrupting operations.
DMARC: Why it matters for aviation
DMARC is an email security protocol designed to protect domain names from being misused by attackers. In simpler terms, DMARC is like an identity check for emails: it verifies that an email claiming to come from, say, @yourairline.com is truly authorized by that domain’s owners and not a forger. It builds on two underlying authentication mechanisms – SPF (Sender Policy Framework) and DKIM (DomainKeys Identified Mail) – to validate emails. Here’s how it works in a nutshell:
- SPF: Allows a domain to publish a list of approved mail servers/IP addresses that are allowed to send email on its behalf. If a message comes from outside that list, it can be flagged as suspicious.
- DKIM: Uses cryptographic signatures to help verify that an email really comes from the claimed domain and has not been altered in transit. When a legitimate email is sent, it’s signed with a private key linked to the sender’s domain. Receiving mail servers can check this signature by retrieving the corresponding public key from the sender's DNS records. If the signature is missing or invalid, it suggests the email may have been forged or modified.
- DMARC: Ties it together by specifying a policy for how to handle emails that fail SPF/DKIM checks. It also requires that the “From” address domain aligns (matches) with the domain authenticated by SPF/DKIM. In essence, DMARC checks “Did this email really come from the domain it claims to be from, according to SPF/DKIM?” If not, what should we do with it?
When you publish a DMARC record in your DNS, you declare a policy (none, quarantine, or reject) and provide addresses to receive reports. These DMARC reports are like flight logs for your email: they tell you which servers are sending emails using your domain and whether those emails passed authentication.
For aviation companies, DMARC is especially important because so much business relies on trusted communications – ticket confirmations, flight operation messages, and maintenance requests.
In addition, DMARC adoption set to a policy of p=reject allows an organization to implement Brand Indicators for Message Identification (BIMI).
A spoofed email that gets through can not only scam people, but even disrupt operational safety (imagine a forged email to airport staff about fuel delivery or a fake “ground stop” notice). DMARC provides a way to ensure only legitimate emails from your domains are delivered, protecting both the business and its customers from impersonation.
What is the difference between DMARC policies?
DMARC policies come in three levels, from weakest to most secure:
- p=none (Monitoring Only): Think of this as “observation mode.” No emails are blocked; all are delivered as normal. However, you receive DMARC reports on email activity. This is useful initially to see who’s sending email using your domain and to troubleshoot authentication, but it does not stop malicious emails. It’s like a surveillance camera – recording incidents but not intervening.
- p=quarantine: At this setting, emails that fail DMARC checks are tagged as suspicious. Mail providers will typically deliver these to the spam/junk folder rather than the inbox. Quarantine offers partial protection – many spoofed emails will avoid the inbox, reducing risk. However, users can still retrieve these messages from spam, and some phishing may sneak through if filters aren’t strict. It’s an improvement, but not foolproof.
- p=reject (full enforcement): This is the recommended, strict policy. Emails that fail authentication are outright rejected – not delivered at all. The receiving mail server will bounce them. This means any unauthorized sender pretending to use your domain will not reach your employees or customers. Reaching p=reject is considered DMARC enforcement because you’re actively blocking fraudulent emails. This is the goal state for true protection. Fortunately, reaching enforcement has been made simple. Airlines and aviation related organizations can now achieve p=reject in just 3 months with Red Sift OnDMARC.
Why choose OnDMARC
As the market-leading DMARC provider, Red Sift is committed to making the internet a fundamentally safer place, and that includes for the aviation industry and its customers. Our dedication to excellence in customer success and award-winning OnDMARC provides a wealth of benefits, including:
- One-click DNS: Configure SPF, DKIM, DMARC, BIMI & MTA-STS in a single place. No manual change requests, no DNS mishaps.
- Dynamic SPF with no 10-lookup limit: Merges lookups, removes macros, and keeps legacy systems plus third-party gateways fully deliverable.
- Continuous DNS hygiene: DNS Guardian flags misconfigured or orphaned subdomains to stop SubdoMailing, dangling DNS, and CNAME takeovers.
- 10x faster troubleshooting: Red Sift Radar is the first large language model (LLM) integrated as standard into OnDMARC, allowing security teams to fix and fix issues 10x faster, without reducing headcount.
- Effortless BIMI adoption: Stand out in the inbox, boost open rates by 39% and brand recall by 44% with ease through implementing a Verified Mark Certificate (VMC) or Common Mark Certificate (CMC).
The consequences of inaction
What if an airline or aviation company decides to delay or only partially implement DMARC? The risks of remaining at p=none or p=quarantine (or having no DMARC at all) are severe:
- Continued domain spoofing: Without DMARC enforcement, attackers can continue to send emails that appear to come from your exact domain – and recipients’ mail systems have no reliable way to tell the difference. For example, if yourairline.com is not protected, a hacker can send an email from “billing@yourairline.com” to customers asking for credit card updates, and those emails will likely be delivered. Your customers and partners remain exposed to phishing and may fall victim, leading to financial loss and erosion of trust.
- Higher success rate for phishing & BEC: Companies that only monitor DMARC (p=none) are essentially observing attacks in the rearview mirror. The phishing emails still land in inboxes. That means the likelihood of a successful attack – a clicked malicious link, a fooled employee, a fraudulent wire transfer remains high. Even p=quarantine isn’t foolproof: a busy employee might check their spam folder and click a phish, or an attacker might craft emails that sometimes evade filters.
- Damage to brand and customer confidence: If you don’t secure your domain, over time customers may start receiving more and more fake emails purporting to be from you. Each incident chips away at your brand’s credibility. In aviation, one phishing scam in your name can become a news headline or go viral on social media. (No airline wants to see “Major Airline X’s customers scammed via spoofed email” in the press.) Lack of DMARC could indirectly lead to loss of business, as wary customers hesitate to open your legitimate emails or click your links, unsure if they’re real.
- Operational and safety risks: Consider that airlines coordinate complex operations via email – from fuel orders to maintenance alerts and crew scheduling. If attackers spoof internal emails or vendor communications, they could potentially cause operational disruptions. For instance, without DMARC, someone could impersonate a vendor and send an urgent invoice change to your finance team (a common BEC tactic), or impersonate an airport official with altered instructions.
- Higher incident response costs: Every phishing email or BEC attempt that gets through might trigger alarms, investigations, and response efforts. Your IT/security team has to spend time chasing down these incidents. This is time and money that could be saved if those emails were blocked from the start.
- Exposure to emerging threats (e.g., SubdoMailing): Failing to adopt DMARC (or neglecting DNS security) leaves you doubly vulnerable to new tricks like SubdoMailing. As covered previously, even if you have DMARC at p=reject, a poorly maintained DNS can be exploited. Organizations that ignore DMARC entirely likely also have lax DNS management, which is a recipe for subdomain takeovers.
Aviation incidents that DMARC could have prevented
It’s worth reflecting on some real incidents to illustrate how DMARC enforcement could have made a difference:
- FACC (Aeronautics Manufacturer) – BEC Fraud: FACC AG was hit by a CEO impersonation email scam in 2016, resulting in a fraudulent €42M transfer. If FACC’s domain had a strict DMARC policy, any email coming from an unauthorized server claiming to be the CEO’s email would likely have failed SPF/DKIM checks and been rejected.
- American Airlines – Phishing Breach: In 2022, American Airlines confirmed that attackers gained access to some employee mailboxes via a phishing campaign. Had American Airlines and its partners all had DMARC enforcement, any phishing email purporting to be from, say, “IT department it@aa.com” sent from a rogue server would fail to deliver. In a broader sense, if all companies adopt DMARC, the overall credibility of phishing emails drops, because fraudulent senders can’t use real domains and have to rely on obviously fake ones.
- Global airline phishing scams: There have been numerous scams where criminals impersonate airlines to defraud the public. One reported scam involved emails offering “free flight tickets” from a major airline if the recipient just paid a small fee – of course, it was fake, and the link stole credit cards (such as Emirates customers).
- Subdomain takeover exploits: While not publicized with specific company names, the large SubdoMailing campaign presumably affected various industries, possibly including travel and aviation. Imagine an airline had a retired subdomain
oldbooking.yourairline.comthat was once used with a third-party vendor and then forgotten. An attacker finds a way to host their service on that subdomain and sends phishing emails to travel agents and customers that pass DMARC (since from the top-level domain’s perspective, that subdomain might be automatically trusted under a lax policy). This could lead to targeted phishing that appears totally legitimate – a worst-case scenario.
Each of these cases reinforces the message: DMARC, when fully enforced, can prevent or mitigate some of the most damaging email threats we’ve seen in aviation. It’s not a silver bullet – users still need training, and other security layers are needed – but DMARC addresses the root of many attacks: fake emails that look real. Removing that threat can break the kill chain of bigger attacks like ransomware or wire fraud that often begin with a simple spoofed email.
Secure your email with Red Sift OnDMARC
Take the next step toward robust email security. Start your 14-day free trial of Red Sift OnDMARC or book a personalized demo with our experts. See firsthand how quickly you can go from no DMARC policy to full DMARC enforcement with the right tool supporting your team. In the demo, we can even show you how many spoofed emails may be targeting your domain without you knowing – and how we can help stop them.
Don’t delay, book now to stay secure!





