What is SubdoMailing?
‘SubdoMailing’, or ‘subdomain emailing’, is a sophisticated tactic that exploits gaps in DMARC safeguards.
In late February 2024, ‘SubdoMailing’ became a trending search term overnight. Research by Guardio Labs uncovered a massive-scale phishing campaign that had been going on since at least 2022. At the time of reporting, the campaign had sent 5 million emails a day from more than 8,000 compromised domains and 13,000 subdomains with several reputable brands having fallen victim to this attack.
SubdoMailing allows attackers to impersonate organizations by sending emails from subdomains pass SPF & DMARC checks, making the messages appear legitimate and deceiving recipients with ease.For instance, a subdomain may be set up to run a service and delegated to a third party via a CNAME alias. If the service is later canceled but the Domain Name System (DNS) configuration remains, a malicious actor could identify the dangling DNS entry, re-create the service, and take control of the DNS name. These subdomain takeovers are typically associated with websites serving unauthorized content under an organization's domain, often overlooking the equally significant risk of email impersonation.
Takeover risks can also arise from configuration errors, such as typos, or when domain names expire while still being referenced in the DNS. In such cases, an attacker can register the expired domain and assume control of the delegated resource. The most severe risk is a nameserver takeover, where an attacker gains control of the domain's nameserver, effectively granting them full access to the entire namespace.
These malicious subdomains are then used to conduct phishing attacks, distribute malware, or steal sensitive information by misleading recipients into believing they are interacting with an authentic organization. With over 333 billion emails sent daily, attackers identified subdomain takeover as a powerful method to exploit trust and manipulate victims into divulging confidential information.
How serious is SubdoMailing?
The scale of SubdoMailing attacks is remarkable, with widespread and severe consequences. Yet, its objective is straightforward: to impersonate trusted brands in order to manipulate recipients into responding. These sophisticated attacks exploit both technical and human vulnerabilities within the Domain Name System (DNS), a fundamental component of internet infrastructure.
How to understand DNS and its role in email communication
To grasp the intricacies of SubdoMailing, it’s crucial to understand the Domain Name System (DNS) and its associated records, including A, AAAA, TXT, MX, and NS records. TXT records are commonly used to store data for various verification protocols, such as the Sender Policy Framework (SPF), which identifies email servers authorized to send emails on behalf of a domain. MX records, on the other hand, direct emails to designated mail servers, ensuring smooth communication between email servers. Misconfigured or outdated entries in these DNS records can expose vulnerabilities, such as allowing unauthorized entities to send emails as the domain owner, bypassing crucial safeguards like DMARC.
What does an attack look like?
Attackers typically take advantage of dangling DNS vulnerabilities in the victim’s estate, often targeting a subdomain with a dangling CNAME pointing to a defunct service. This allows them to authorize themselves to send emails on behalf of the victim’s domain.
For added legitimacy, attackers may host a convincing replica of the impersonated website or simply redirect traffic to the real website of the targeted domain. 'SubdoMailing' attacks typically occur via two methods:
- Directly gaining control over the DNS records of a domain or subdomain belonging to the victim.
- Indirectly exploiting the SPF record of a domain or subdomain.
In both cases, attackers take advantage of dangling DNS vulnerabilities, such as unused or defunct DNS records within the victim’s infrastructure, that can be taken over to facilitate the attack.
Dangling vulnerabilities
Previously legitimate DNS records: Usually CNAMEs previously used for hosted services, but can also be NS delegations, A/AAAA records pointing to IP addresses, MX records and even nameservers of domains.
Typos: Many services have common typos that are noticed by attackers and registered by attackers. This also serves the purpose of hiding in plain sight as typos are easily overlooked.
Setup & documentation errors: Misunderstandings when setting up a service can lead to documentation examples being blindly copied over. If those examples are not kept registered, attackers can register them instead.
How they are exploited?
Expired domain: Attackers identify expired or otherwise non-registered domains that are referenced by dangling vulnerabilities and register them for themselves, giving them control over the records.
Service takeover: A subdomain or domain is pointing to some kind of service (SaaS, PaaS, IaaS) that they are no longer using such as a helpdesk, shop, blog or other infrastructure. The service allows the attacker to take control of the subdomain or domain without proving ownership. This also includes hosted services that give control of IP addresses, or simply taking ownership of IP addresses directly.
All of these can be mixed and matched and chained together infinitely.
Examples of how SubdoMailing attacks can work
SPF record including expired domain of previously used service
Vulnerability: example-company.com has an SPF record containing “include:email-saas.com”, a no longer in business SaaS that provided email services. Once the email-saas.com domain eventually expires, the attacker can re-register it and return their own IPs for the SPF include.
Impact: The attacker can serve their own SPF record, with their own IPs, allowing them to send SPF-authorized-and-aligned, DMARC compliant email as From: example-company.com.
CNAME to expired domain of previously used service
Vulnerability: analytics.example-company.com is a CNAME that points to analytics-saas.com, a former SaaS that provided Analytics services that went out of business. The domain eventually expires allowing the attacker to re-register it and take control of analytics.example-company.com.
Impact: The attacker can now serve A/AAAA, TXT and MX records for analytics.example-company.com allowing them to host a website there as well as receive emails for it, and send SPF-authorized-and-aligned, DMARC compliant emails as From: @analytics.example-company.com. If example-company.com’s DMARC policy does not have strict SPF alignment (“aspf=s”) they can also send as From: @example-company.com
Why does this type of attack happen?
This attack exploits a combination of human error and overlooked vulnerabilities, often stemming from a lack of deep understanding of the DNS and how it interacts with email standards such as DMARC, SPF & DKIM. Some of these issues can be addressed through improved technical practices, while others require better awareness and training to avoid unintentional mistakes. Key weaknesses include:
Inherited authentication
When a compromised domain or its subdomain is included in an SPF policy, authentication protocols like SPF and DMARC are often automatically inherited. This happens because DNS CNAME records point to the destination's DNS zone, enabling attackers to send authenticated emails under the guise of the legitimate domain.
Expired domain registrations
Human oversights, such as missing domain renewal deadlines, or simply letting domains expire due to a business believing they don’t use or need it anymore can leave domains vulnerable to takeover. With around 70% of domains abandoned after the first year, attackers have abundant opportunities to exploit these expired domains.
DNS hygiene
When a service is no longer used, its configuration is often overlooked, leaving behind forgotten or dangling DNS records & SPF includes. These neglected configurations can result in domain or subdomain takeovers, and in extreme cases, allow attackers full control of a nameserver.
Human fallibility
People make mistakes, sometimes by unintentionally introducing vulnerabilities, other times by failing to consider the risk of seemingly harmless elements. Example domains in documentation or a simple typo when adding a record can open the door to exploitation. This underscores the need for proactive education and robust processes to mitigate risks.
Dangling DNS configuration: Records at risk
Certain DNS resource types are more prone to misconfiguration, which can lead to security vulnerabilities. Here's an overview of key types and their associated risks:
- A and AAAA records: These map DNS names to IP addresses, with A records for IPv4 and AAAA for IPv6. Misconfigured or outdated IP mappings can lead to vulnerabilities.
- CNAME records: Used to create aliases, they delegate DNS configurations to another name. Often used for third-party services, mismanagement of CNAMEs can lead to unauthorized control over the domain.
- MX records: These direct emails to designated mail servers. If a mail server is taken over, attackers can intercept or manipulate domain email traffic.
- NS records: These list the authoritative nameservers for a DNS zone. If any entry points to an attacker-controlled server, the attacker gains full control over all queries to that zone.
- SPF records: These specify email-sending policies. If the referenced names or IP addresses are compromised, attackers can spoof emails from the domain.
Properly managing these DNS records is essential to prevent unauthorized access, data leakage, or service disruption.
How to secure your domain
- Renew domain registrations: Never allow previously registered domains to expire. The cost of maintaining domains is minimal compared to the expense and effort of addressing vulnerabilities caused by expired domains - even if the product/service may no longer exist or was rebranded.
- Clean up your DNS often: Remove unused resource records and redundant third-party dependencies from your DNS. Schedule regular audits with your infrastructure team to ensure your DNS remains secure and up to date.
- Use a trusted email protection provider like Red Sift: Partner with a reliable vendor for managing DMARC, DKIM, SPF, and MTA-STS. A proactive vendor can notify you of anomalies, such as void or compromised domains within your SPF policy.
- Check for dangling DNS records: Maintain a comprehensive inventory of your hostnames and monitor for dangling records or inactive third-party services. When detected, promptly remove them to prevent exploitation. Include this workflow in your Security Operations Centre (SOC) to streamline remediation.
- Monitor domain sending activity: Ensure you can quickly identify if emails are being sent from compromised domains or subdomains. Choose an email protection vendor capable of providing real-time alerts for all sending sources.
- Watch your supply chain’s domains: Regularly monitor the primary domains of your infrastructure supply chain, especially those listed in your SPF policy. If abandoned domains are re-registered or services become available again, take immediate action to mitigate risks.
The best tools for checking whether you’ve been impacted by SubdoMailing
Red Sift Investigate
If you’re wondering if you’ve been impacted by SubdoMailing, the best place to start is Red Sift Investigate. All you need to do is send the tool an email and it will dynamically check your email-sending service for any misconfigurations or exposures in real-time.
Red Sift SPF Checker
Should Investigate reveal any ‘SubdoMailers’ – also known as poisoned includes – it will prompt you to view them and the rest of your SPF setup in the Red Sift SPF Checker. The tool allows you to pinpoint any poisoned includes in a dynamic visualization of the ‘SPF tree’, helping to speed up remediation efforts.
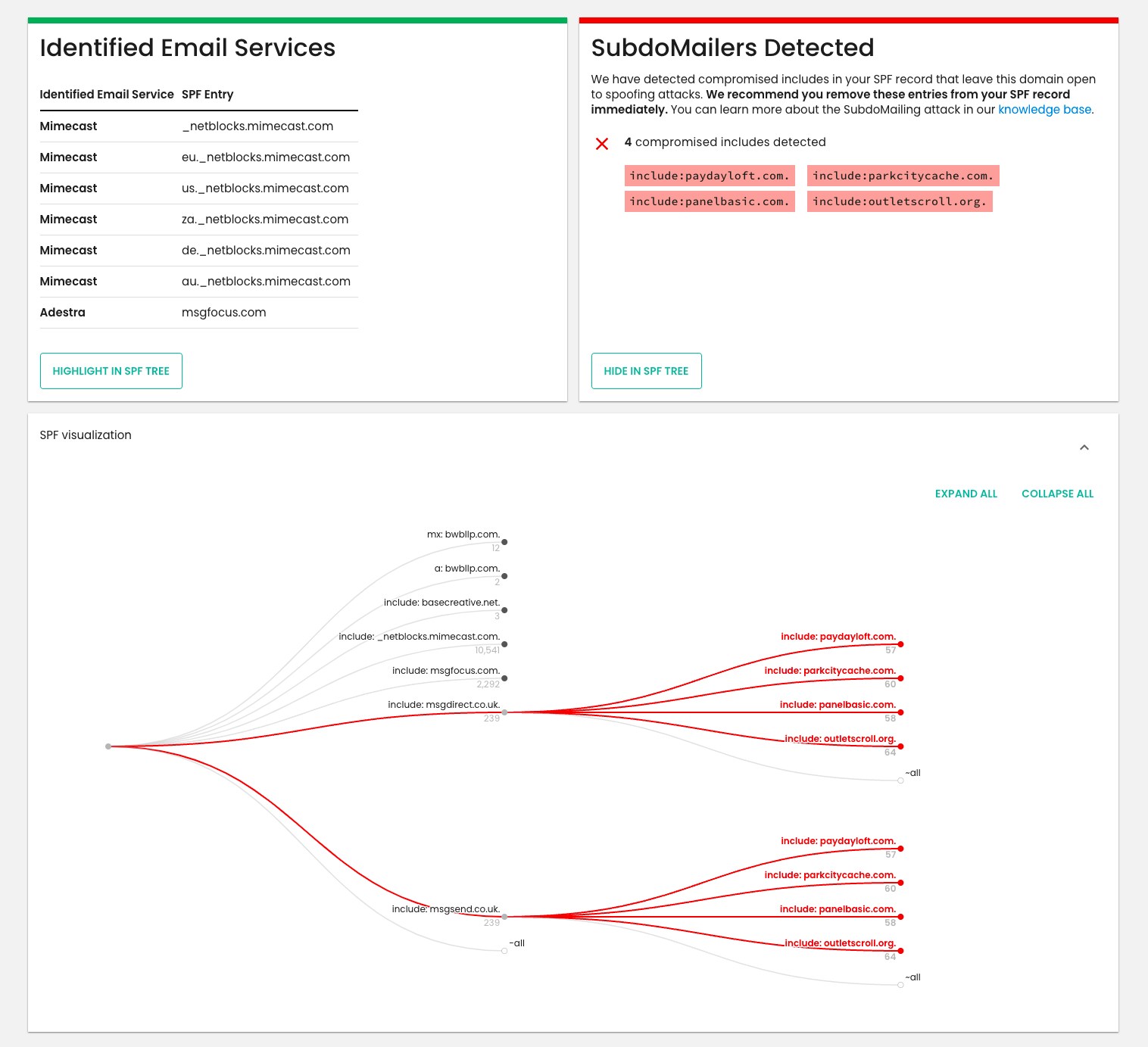

We’ve distilled all of our findings from our ‘known bad list’ so that any domain in the world can be checked to see if their SPF includes are poisoned. We are continuously working on expanding the list – it has grown 500% in one week and we are finding more domains every day.
To learn more about SubdoMailing and how Red Sift discovered and protected its customers against the attack, read our article.
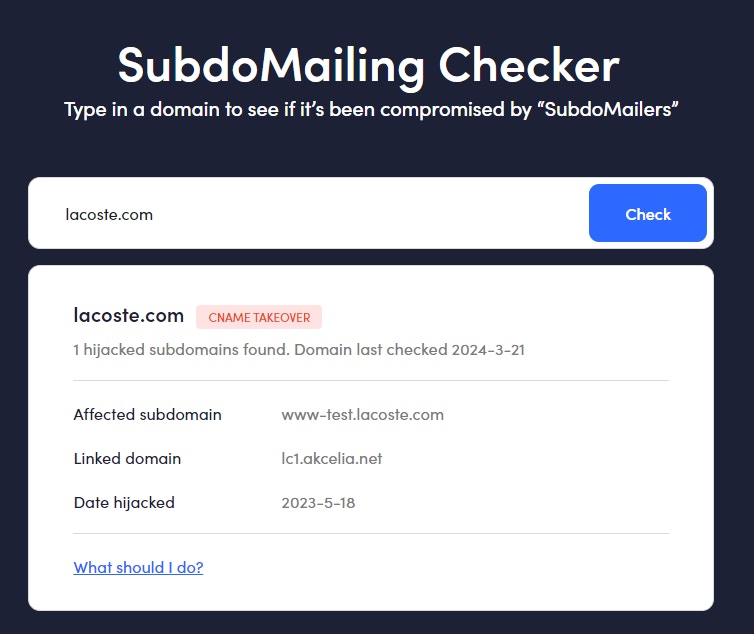
Guardio Labs’ SubdoMailing Checker
Guardio released a SubdoMailing Checker tool that quickly allows users to check if a domain has been compromised. It flags the affected subdomain and the date it was hijacked, along with clear guidance on how to protect your domain in the future.

Static checks for SPF
Many free tools on the internet like MX Toolbox or EasyDMARC’s SPF Tool can look at your DNS records to see if you have a valid SPF record. Since SPF information is publicly available, these tools start with your domain and check if a valid SPF record is published in the DNS. However, these tools won’t tell you whether your SPF setup has been impacted by SubdoMailing. Instead, you would be required to carry out manual checks.
If you have DMARC reporting, you would have to go through your reports and look for suspicious or unknown senders passing SPF. This would indicate that something suspicious is going on.
This is how one of our very experienced Customer Success Engineers discovered an early instance of SubdoMailing in our customer base. He noticed mail was coming from a sender with a poor reputation and a subdomain that appeared unrelated to our customer’s main domain. This subdomain had a CNAME and pointed to an SPF record authorizing services he had never seen. To read the full story of what he uncovered and the next steps that were taken, keep on reading here.
If you don’t have DMARC reporting, you have no visibility into your SPF pass rate, which makes checking for exposures very difficult. To carry out a check, you’d need to analyze each one of your SPF mechanisms and their IPs manually and check various databases to see if they are blocklisted, have bad reputations, or have been used in attacks. In addition, you’d have nothing to compare your current SPF mechanisms against and you wouldn’t know which are active versus which are old or redundant and can be removed.
Both of these methods are time-consuming and complex, especially for organizations that lack IT resources or expertise.
For ongoing protection, Red Sift has you covered
Comprehensive attack surface monitoring with Red Sift ASM
Red Sift ASM continuously identifies and monitors assets vulnerable to attacks like SubdoMailing. It scans domains and subdomains, inspects DNS, email, and web configurations, and flags risks such as domain expiration and dangling DNS records. Real-time asset discovery ensures your team is immediately informed of vulnerabilities, enabling prompt action to secure your DNS and prevent exploitation.
Email activity oversight with Red Sift OnDMARC
Red Sift OnDMARC provides complete visibility into all outgoing emails, enabling quick identification of unauthorized senders using your domain or subdomains. It also gives detailed insights into SPF policy configurations, highlighting raw and nested includes for better management.
In July 2024, Red Sift introduced DNS Guardian, a pioneering feature that continuously monitors domains for misconfigurations, protecting against SubdoMailing attacks, dangling DNS records, and CNAME takeovers. Red Sift OnDMARC is the only DMARC vendor on the market to offer DNS configuration-checking capabilities.
Streamline email authentication with Dynamic Services, part of Red Sift OnDMARC
Dynamic Services streamlines SPF, DKIM, DMARC, and MTA-STS implementation by replacing static DNS records with smart, self-healing configurations. This eliminates manual updates with DNS providers and ensures continued email authentication, even if a domain in your SPF policy becomes void. Dynamic Services detects and resolves issues automatically, maintaining robust email security in complex environments.
Ready to get started?





