Red Sift’s definitive guide to email security

- SPF and DKIM
- What is Sender Policy Framework (SPF)?
- How does SPF work?
- What is an SPF lookup?
- What is an SPF include?
- What is the SPF lookup limit?
- How can I overcome the SPF lookup limit?
- Why does my SPF record fail?
- What is DomainKeys Identified Mail (DKIM)?
- How does DKIM work?
- What is a DKIM signature?
- What is a DKIM key?
- Is DKIM necessary for secure email?
- What is the difference between SPF and DKIM?
- SPF and DKIM
- What is Sender Policy Framework (SPF)?
- How does SPF work?
- What is an SPF lookup?
- What is an SPF include?
- What is the SPF lookup limit?
- How can I overcome the SPF lookup limit?
- Why does my SPF record fail?
- What is DomainKeys Identified Mail (DKIM)?
- How does DKIM work?
- What is a DKIM signature?
- What is a DKIM key?
- Is DKIM necessary for secure email?
- What is the difference between SPF and DKIM?
SPF and DKIM
What is Sender Policy Framework (SPF)?
Sender Policy Framework (SPF) is an email authentication protocol designed to stop attackers from sending emails that appear to come from your domain. An SPF policy tells receiving mail servers which sending sources are legitimate for your domain, helping prevent email spoofing, phishing, and domain impersonation. SPF is now a baseline requirement for organizations sending bulk email in 2026.
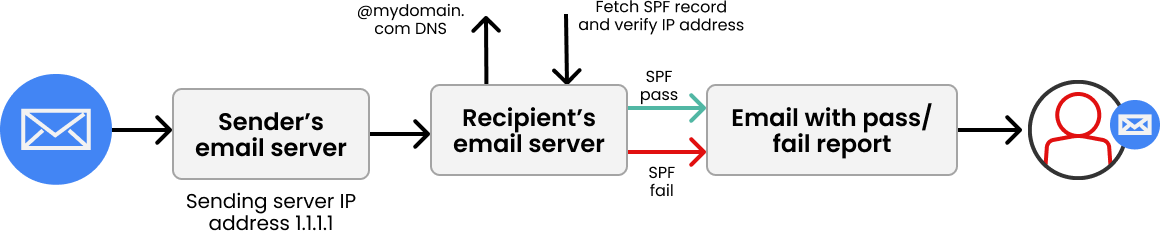
How does SPF work?
Your SPF policy is published in your Domain Name System (DNS) as a TXT record, listing the mail servers (IP addresses) authorized to send on your behalf. When an email is sent, the recipient’s mail server checks this policy to confirm whether the sending IP address is approved. If it matches, the message is delivered; if not, it may be flagged as spam or rejected.

What is an SPF lookup?
An SPF lookup is when the DNS receiving your email has to ‘look up’ the IP addresses present in any of the include statements within your record, to check if they match with the IP sending your email.
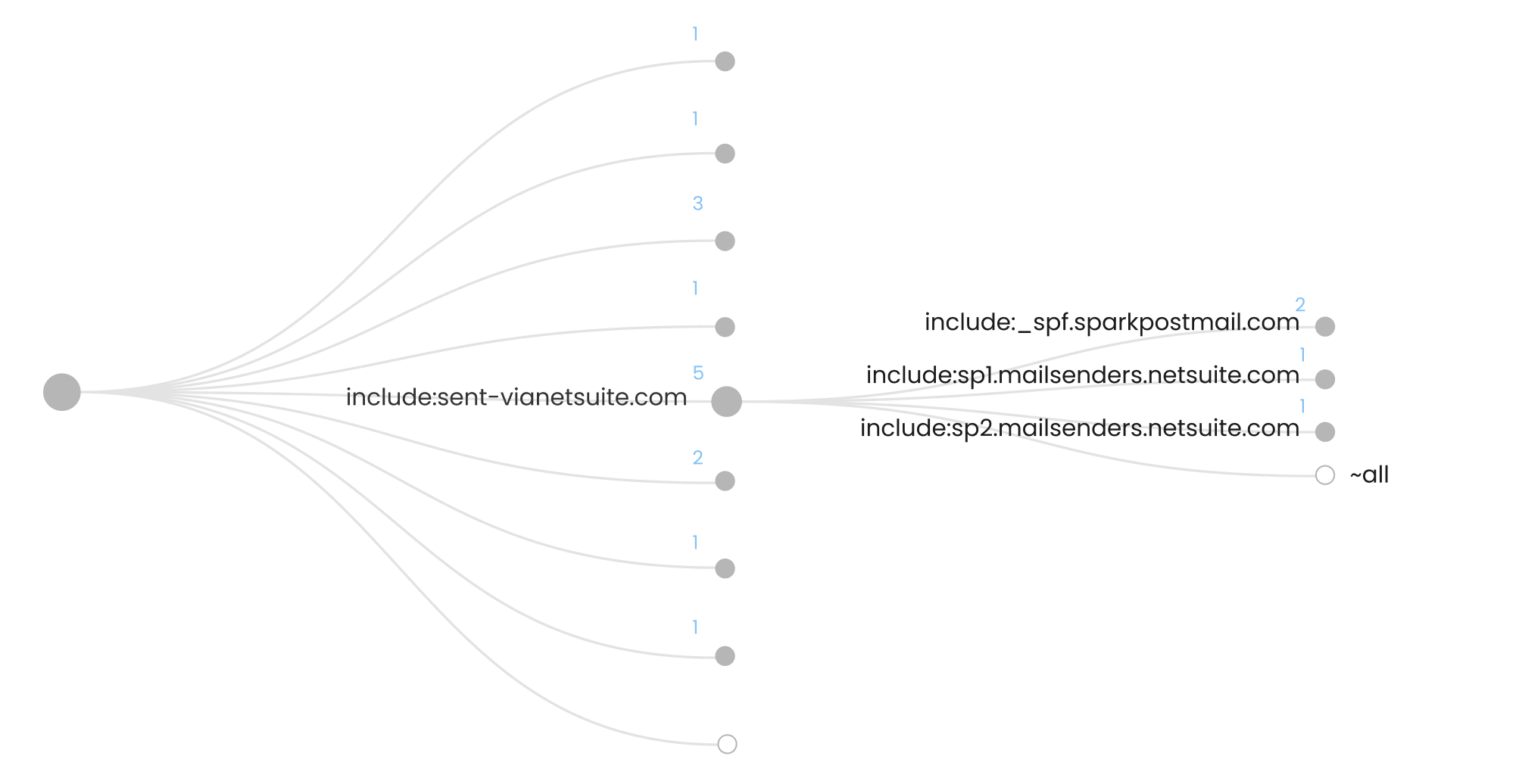
What is an SPF include?
An SPF include is a feature within SPF records that allows domain owners to include the SPF records of other domains in their own SPF policy. This enables streamlined management and ensures that the included domains' email sending policies are considered when determining the legitimacy of emails sent from the including domain.
What is the SPF lookup limit?
The SPF lookup limit is the number of times a recipient DNS can carry out a lookup for a domain with a maximum cap set at 10.
You can add unlimited singular IP addresses to your record without incurring additional DNS lookups, as they are directly visible in the record.
But this isn’t the case for include statements, and the number of IP addresses an include has equals the number of lookups the receiving DNS has to carry out. This contributes to your maximum total of 10.
So for example, you might have 3 IP addresses listed in your SPF record as they are, an include statement for Google (which contains 4 IP addresses) and an include statement for Mimecast (which contains 6). The receiving DNS doesn’t need to carry out lookups for the visible IPs, but it does for the Google and Mimecast include statements. So in this case, you’ve reached your total of 10.

How can I overcome the SPF lookup limit?
In reality, 10 lookups aren’t enough, because most businesses use a number of tools that send emails on their behalf. These will all have their own include statements, which will include IP addresses, and so will require lookups. If you go over the limit, then you’ll likely fail authentication and your deliverability will suffer. By 2026, dynamic SPF solutions have become the recommended approach for managing this limitation, replacing manual SPF flattening methods that require constant maintenance.
Why does my SPF record fail?
One of the main reasons the SPF record might be failing for your email traffic is the “too many DNS lookups” error. The SPF specification limits the number of DNS lookups to 10. If your SPF record results in more than 10 DNS lookups then SPF will fail. The SPF mechanisms counted towards DNS lookups are: a, ptr, mx, include, redirect and exists. “ip4”, “ip6” and “all” do not count towards the lookup limit.
If that all sounds a bit too technical, think about it this way. G Suite alone takes up 4 DNS lookups, add in Hubspot for marketing which uses 7 lookups then you’ll already be over the 10 lookup limit! As soon as you go over 10 SPF lookups, your email traffic will begin to randomly fail validation. This is why organizations in 2026 are shifting to dynamic SPF management rather than trying to manually maintain flattened records.
What is DomainKeys Identified Mail (DKIM)?
DKIM stands for DomainKeys Identified Mail, which is an email authentication protocol designed to prevent message modification in transit, a method often used in phishing and email scams.
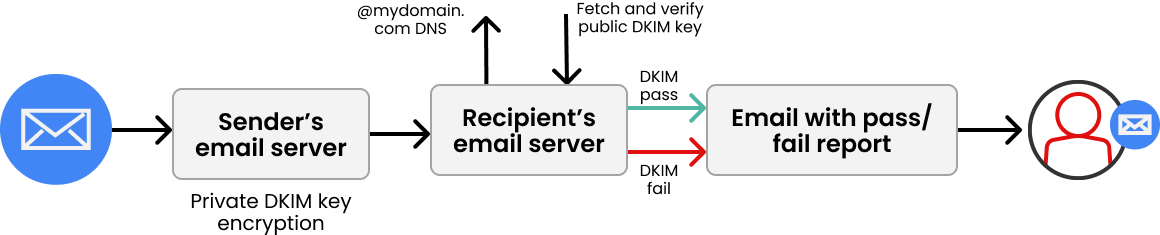
How does DKIM work?
DKIM is a more recent standard and more complex than SPF. Its functionality is based on using asymmetric cryptography in the signature parts of the email. There is a private key stored on the server that sent the email, a place where it could never be read by the end-user, and a public key which is published in the DNS record of the sender’s domain and is used to decrypt email signatures.
In other words, when an email is composed, its headers and body are signed using the private key of the sender to create a digital signature, which is also sent as a header field along with the email. On the receiver’s side (if DKIM is enabled), the server retrieves the public key and verifies if the email was indeed signed by the sending domain. If the signature is successfully validated, that proves that the sending domain sent the message and also that the headers and body of the message have not been modified or tampered with during transmission.

What is a DKIM signature?
A DKIM signature is a unique cryptographic value embedded in the header of an outgoing email. Generated using the sender’s private DKIM key, this signature allows the recipient’s mail server to retrieve the corresponding public key from DNS and confirm that the message was sent from an authorized source and that its content has not been altered in transit.
What is a DKIM key?
A DKIM key is the cryptographic key pair used in DKIM authentication. The private key is securely stored on the sending mail server and used to generate the DKIM signature for each outgoing email. The public key is published in the sending domain’s DNS as a TXT record, allowing receiving servers to verify the signature and confirm the email’s integrity and authenticity.
Get the in-depth scoop on all things DKIM in our technical configuration guide.
Is DKIM necessary for secure email?
Yes. DKIM (DomainKeys Identified Mail) is a critical email authentication protocol that protects against spoofing, phishing, and message tampering. It adds a cryptographic signature to each outgoing message, enabling receiving servers to verify that the email’s content hasn’t been altered and that it comes from an authorized domain. DKIM is also a core component of the DMARC verification process, working alongside SPF to enforce domain alignment and strengthen email security. Major inbox providers now require DKIM for bulk email senders, making it essential for deliverability in 2026.
What is the difference between SPF and DKIM?
SPF (Sender Policy Framework) verifies that an email is sent from an IP address authorized by the sending domain’s SPF record. DKIM (DomainKeys Identified Mail) uses a cryptographic signature, validated via a public key in DNS, to confirm that the email’s content hasn’t been altered and that it comes from an authorized domain. SPF focuses on sender authorization, while DKIM ensures message integrity and authenticity.


Frequently asked questions: Email security guide
All email security measures (apart from DMARC) are ineffective at spotting a malicious email when it appears to come from a legitimate domain. This is because of a flaw in Simple Mail Transfer Protocol (SMTP). In October 2008, the Network Working Group officially labelled it 'inherently insecure', stating that anyone could impersonate a domain and use it to send fraudulent emails pretending to be the domain owner.
Anyone with a very basic knowledge of coding can learn the steps required to impersonate someone's email identity through a quick Google search. The result is an email that looks legitimate without typical phishing indicators. With 3.4 billion phishing emails sent every day, email systems remain the prime target for cybercriminals.
SPF (Sender Policy Framework) verifies that an email is sent from an IP address authorised by the sending domain's SPF record through a DNS TXT record listing authorised mail servers.
DKIM (DomainKeys Identified Mail) uses a cryptographic signature, validated via a public key in DNS, to confirm that the email's content hasn't been altered and comes from an authorised domain. Both are essential to email security, but neither prevents exact impersonation.
While the protocols tell the recipient who the email is from, the recipient has no instruction to act on this knowledge. Major inbox providers now require SPF and DKIM for bulk email senders in 2026.
DMARC stands for Domain-based Message Authentication, Reporting, and Conformance. It's an outbound email security protocol that allows domain owners to tell receiving inboxes to reject spoof emails. DMARC works by combining the results of SPF and DKIM to determine if your email is authentic and authorised.
The DMARC policy (defined by the "p=" tag in your DNS record) then tells recipient servers what to do with it. DMARC stops exact domain impersonation by instructing recipient servers not to accept any emails which aren't authenticated. In 2026, DMARC has become a standard requirement for organisations sending bulk email.
The SPF specification limits DNS lookups to 10. If your SPF record exceeds this, SPF will fail. The SPF mechanisms counted are: a, ptr, mx, include, redirect and exists. In reality, 10 lookups aren't enough because most businesses use multiple email-sending tools.
G Suite alone takes up 4 DNS lookups, add in HubSpot for marketing which uses 7 lookups and you're already over the limit. As soon as you go over 10 SPF lookups, your email traffic will begin to randomly fail validation. This is why organisations in 2026 are shifting to dynamic SPF management rather than trying to manually maintain flattened records.
Mail Transfer Agent Strict Transport Security (MTA-STS) is a standard that enables the encryption of messages being sent between two mail servers. It specifies that emails can only be sent over a Transport Layer Security (TLS) encrypted connection which prevents interception by cybercriminals. SMTP alone does not provide security, making it vulnerable to man-in-the-middle attacks where communication is intercepted and possibly changed.
Additionally, encryption is optional in SMTP, meaning emails can be sent in plaintext. Without MTA-STS, an attacker can intercept the communication and force the message to be sent in plain text. In 2026, MTA-STS has become a standard security control for organisations handling sensitive communications.
By implementing DMARC you benefit from stopping phishing attempts that appear to come from you, stronger customer trust, reduced cyber risk and compliance with bulk sender requirements from Google, Yahoo and Microsoft.
DMARC strengthens compliance with PCI DSS 4.0 and enhances overall organisational resilience against evolving cyber threats. Once at p=reject (enforcement), DMARC blocks vendor fraud, account takeovers, and email spoofing by stopping bad actors from using your domain to send phishing emails and carry out Business Email Compromise (BEC). According to Verizon's 2025 Data Breach Investigations Report, BEC attacks constitute more than 17-22% of all Social Engineering incidents.
Red Sift OnDMARC accelerates the DMARC journey with automated sender discovery, prescriptive fixes, anomaly detection, and role-based access for global teams. By 2026, leading platforms enable enterprises to reach p=reject enforcement in 6-8 weeks rather than the six month timelines once typical.
One of the most commonly reported benefits of OnDMARC is an average time of 6-8 weeks to reach full enforcement. The platform's powerful automation continuously analyses what's going on across your domain, surfacing alerts for where and how to make necessary changes. Within 24 hours of adding your unique DMARC record to DNS, OnDMARC begins to analyse and display DMARC reports in clear dashboards.
Major email providers including Microsoft, Google, and Yahoo now mandate DMARC for bulk senders (organisations sending 5,000+ emails per day) as of 2024-2025, and these requirements have become standard in 2026.
Beyond inbox provider requirements, certain industries and government regulations are moving toward mandating DMARC. U.S. federal agencies are required to use DMARC, as are DORA regulated payment processors. Additionally, DMARC implementation strengthens compliance with regulations including PCI DSS 4.0, GDPR, and NIS2. For cybersecurity, email security and IT teams, ensuring your organisation's email security aligns with international best practices and requirements is essential.





