Complete visibility
Get a view into your entire attack surface – including assets you didn't know existed.


Discover and build a full inventory of your external-facing and cloud assets, including those previously unknown, and monitor them for misconfigurations continuously.

















































Red Sift ASM (Attack Surface Management) continuously discovers, inventories and helps manage your business’s critical external-facing and cloud assets.
Get a view into your entire attack surface – including assets you didn't know existed.
Be aware of and remediate configuration risks before bad actors can take advantage.
Solve problems before they are visible to your insurer.
Stay aligned with best practices, frameworks and legislation.

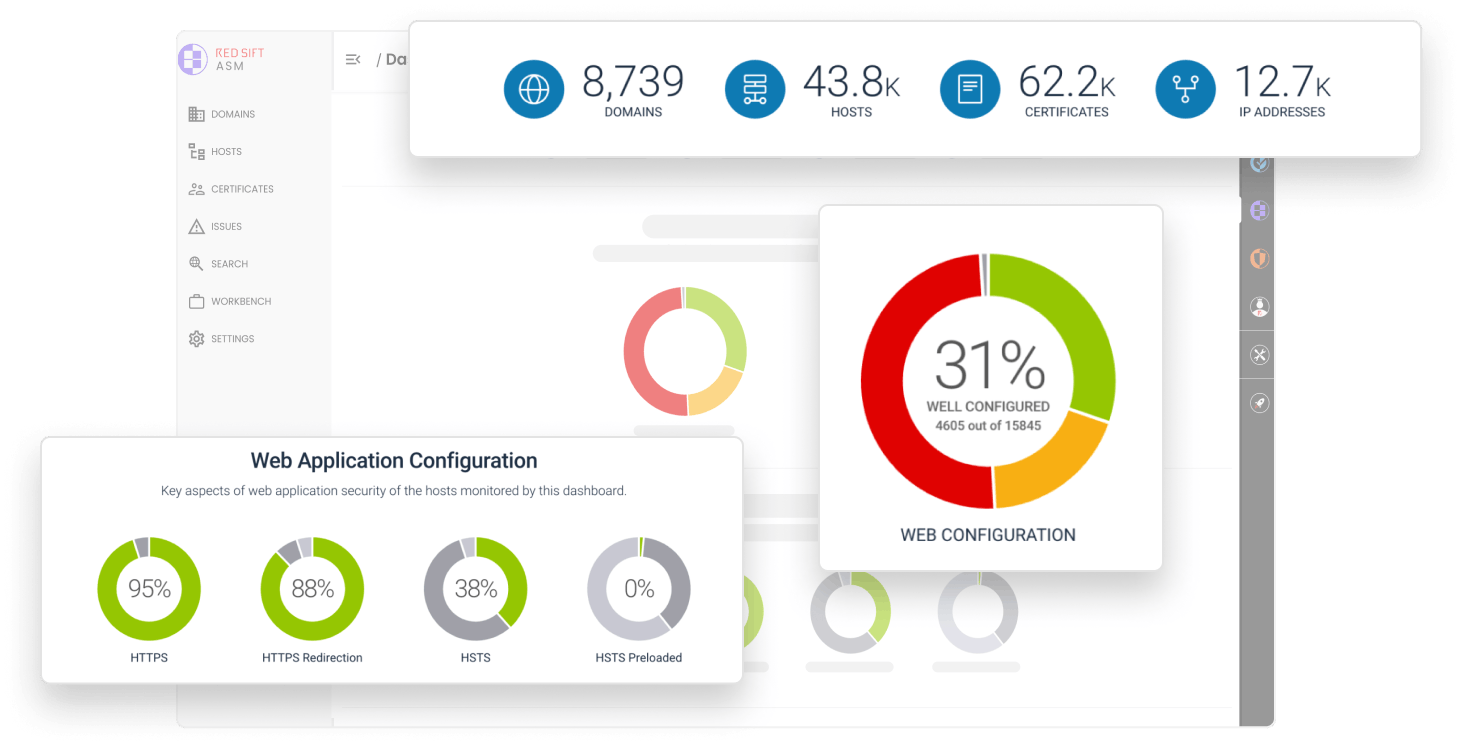
Identify mismanaged or unmanaged assets that other tools miss. Red Sift ASM continuously scans domains, hostnames, and IP addresses so your data is always fresh.
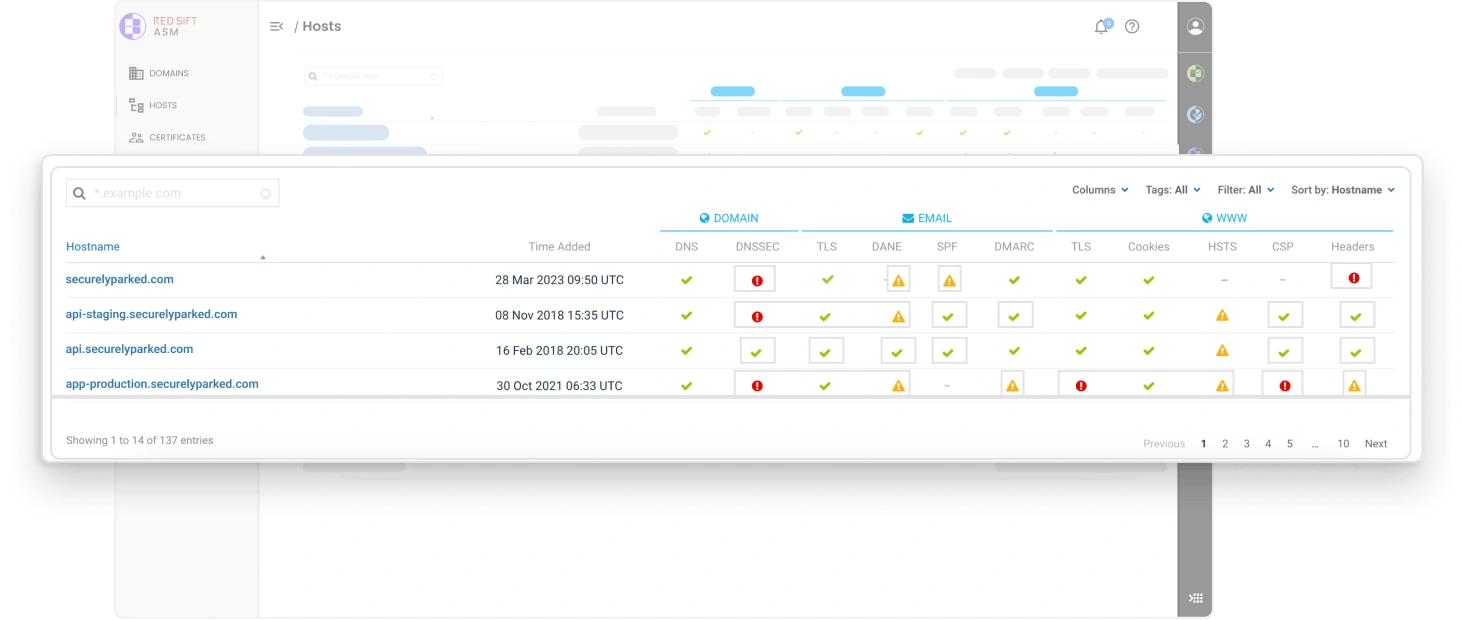
Build an inventory of your external-facing and cloud assets without spreadsheets or manual processes. Connect to cloud providers, certificate authorities, registrars, and managed DNS providers to import and monitor all of your assets.
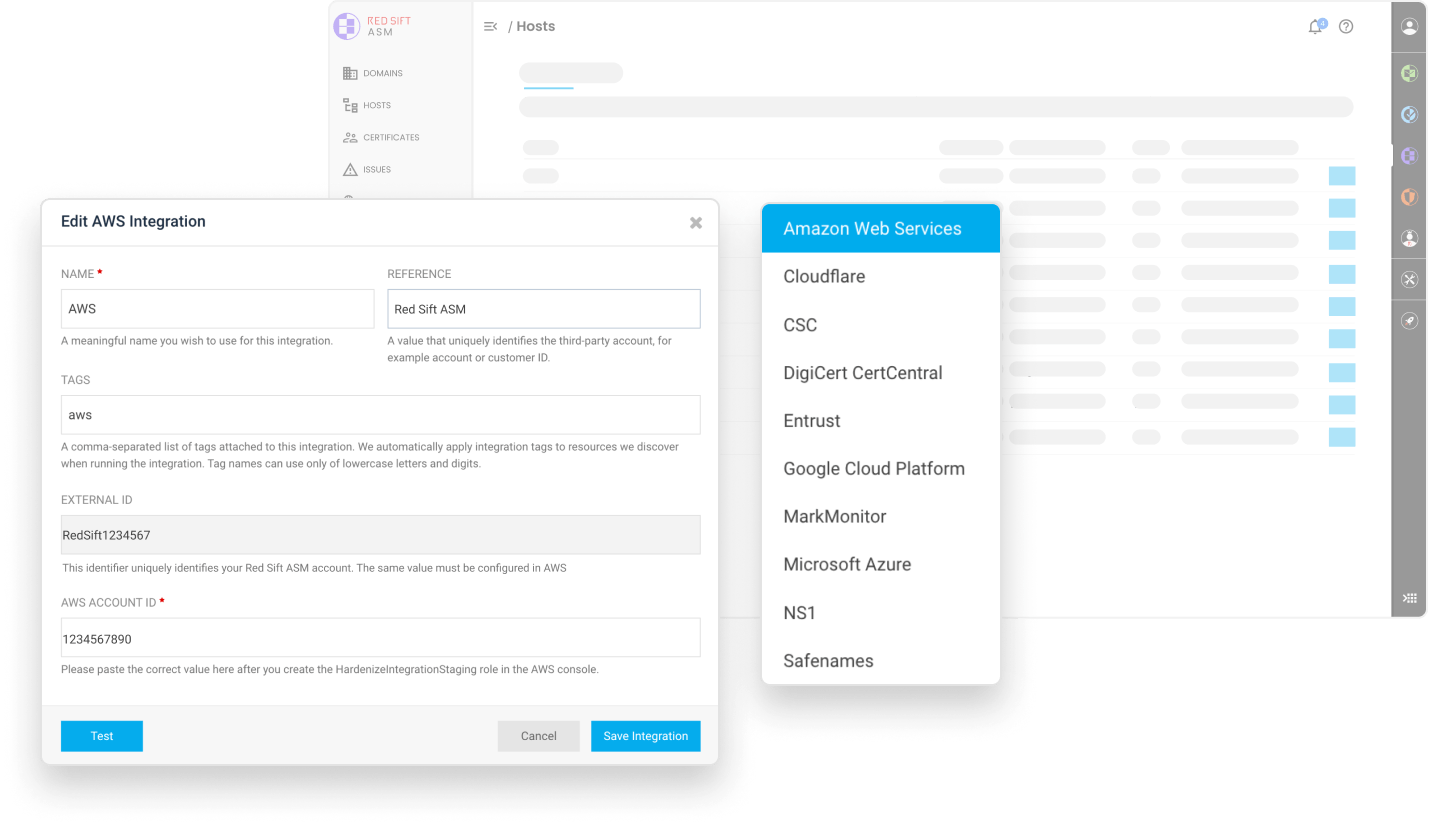
Integrate with AWS, Google Cloud and Azure out-of-the-box for a more holistic view of the entire attack surface.
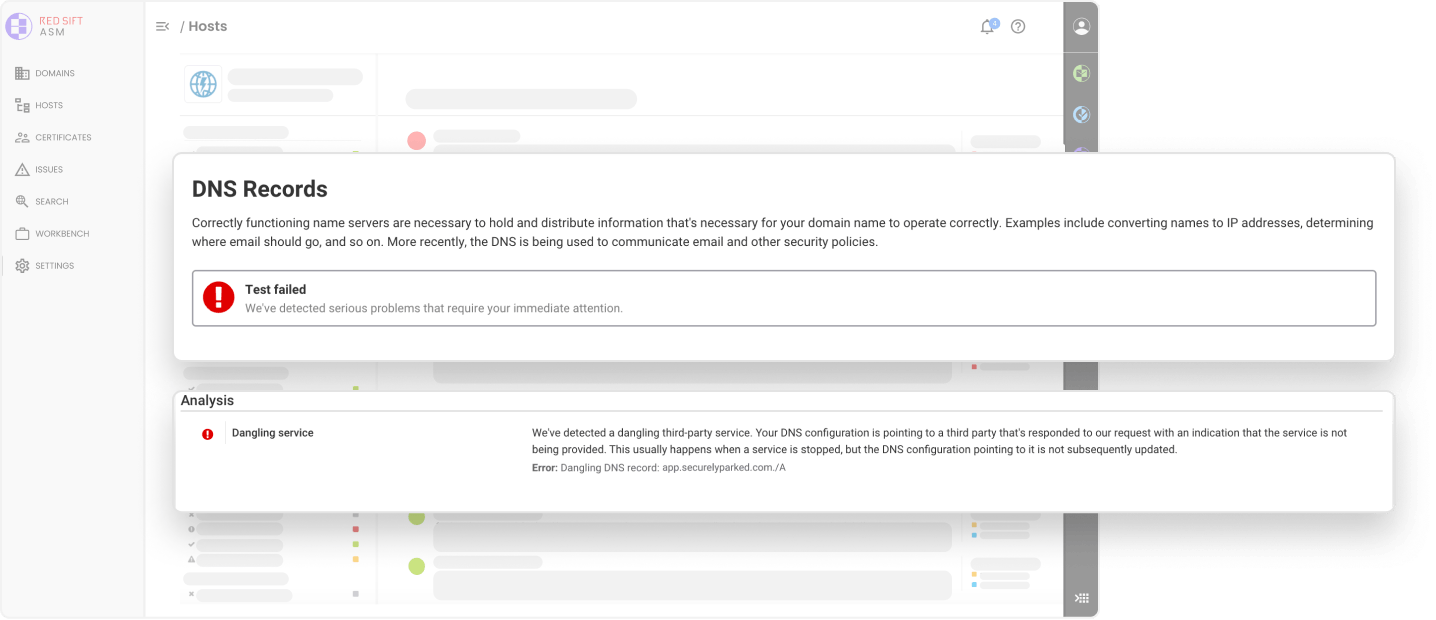
In-depth, real-time data about each asset makes it straightforward to take action as soon as a misconfiguration or unmanaged asset is identified.

Monitor your DNS and DNSSEC configuration across your estate. Identify dangling DNS issues that could be a subdomain takeover risk. Validate your DANE configuration.

Check for all known SSL and TLS protocols, cipher suites, named groups, and other cryptographic primitives. Simulate connections from popular clients to understand what they will negotiate with your sites.

Deploy all the relevant standards, such as HSTS, CSP, SRI, and others. Use secure cookies, including name prefixes and same-site cookies. Prevent mixed content.

Check for STARTTLS and correct TLS and PKI configuration. Deploy SPF, DMARC, and MTA-STS with confidence.
![[object Object]](https://red-sift.cdn.prismic.io/red-sift/07450bf0-7008-41f5-91a9-0ca31822d3da_Quote+Open.svg)

Trusted by the best security leaders in the business




"Coop uses Red Sift ASM to gain better visibility of our exposure on the internet. We use it to discover and monitor all of our cloud apps and third-party certificates. It also helps us validate our WebServer settings such as CSP and HSTS headers to harden our configurations."

Red Sift ASM & Red Sift Certificates automatically combines external-facing and cloud asset information with certificate data and seeds this information into the Red Sift Platform automatically.
Find out more about Certificates
Red Sift ASM & Red Sift Brand Trust help you discover and protect your know, unknown and lookalike assets. Findings are shared across tools to give you the most complete view of your entire attack surface.
Find out more about Brand Trust