Introducing Red Sift Radar Lite
Security scanning tools have a usability problem. Many excel at checking configurations and flagging issues—they'll tell you your TLS version is outdated, your SPF record has syntax errors, or your DMARC policy is set to "none"—but they don't prioritize intelligently, guide remediation, or speak plainly.
Which issue should you tackle first? What happens if you don't fix it? For non-specialists, understanding why something like a "missing HSTS directive" matters requires extra research.
The result: teams fix what's obvious or urgent-looking, while higher-impact issues that require context are delayed or missed. For smaller IT teams without dedicated security personnel, this creates a barrier to entry. For power users at larger organizations, it adds friction by pulling time away from remediation and into report analysis.
To address this, we’ve launched Red Sift Radar Lite, a free, AI-powered security analysis tool that evaluates your domain’s email authentication, DNS, and website security settings, highlights what needs fixing, and benchmarks your posture against your industry peers. It serves as a lightweight introduction to Radar, our full-scale LLM, which integrates directly with Red Sift applications to operate with contextual understanding of your environment and support deeper, ongoing security analysis.

How Radar Lite works: Turning security questions into actionable insight
Radar Lite is designed to bridge the gap between raw security checks and real-world decision-making. You start by asking a question in natural language, for example, “Is my domain securely configured?” or “Check the DMARC configuration of my domain.”

Radar Lite interprets that question and runs the appropriate set of checks across email authentication (SPF, DKIM, DMARC, and related controls), DNS configuration, TLS and certificates, and key web security headers. It understands how these controls depend on one another, so issues are evaluated in context rather than in isolation.
Once the checks are complete, Radar Lite analyzes the results to determine what actually needs attention first. Prioritization considers configuration dependencies, common compliance requirements, and the severity of real-world risk. Each finding explains not just what is wrong, but why it matters and what the impact could be if it’s left unresolved.
To put those findings into context, Radar Lite also benchmarks your domain against relevant peers. It does this on demand by analyzing your website and using AI to classify it within our industry taxonomy. That classification is then compared against thousands of well-known domains in the same category that we’ve analyzed previously, allowing Radar Lite to show how your setup compares to what’s typical across your sector.
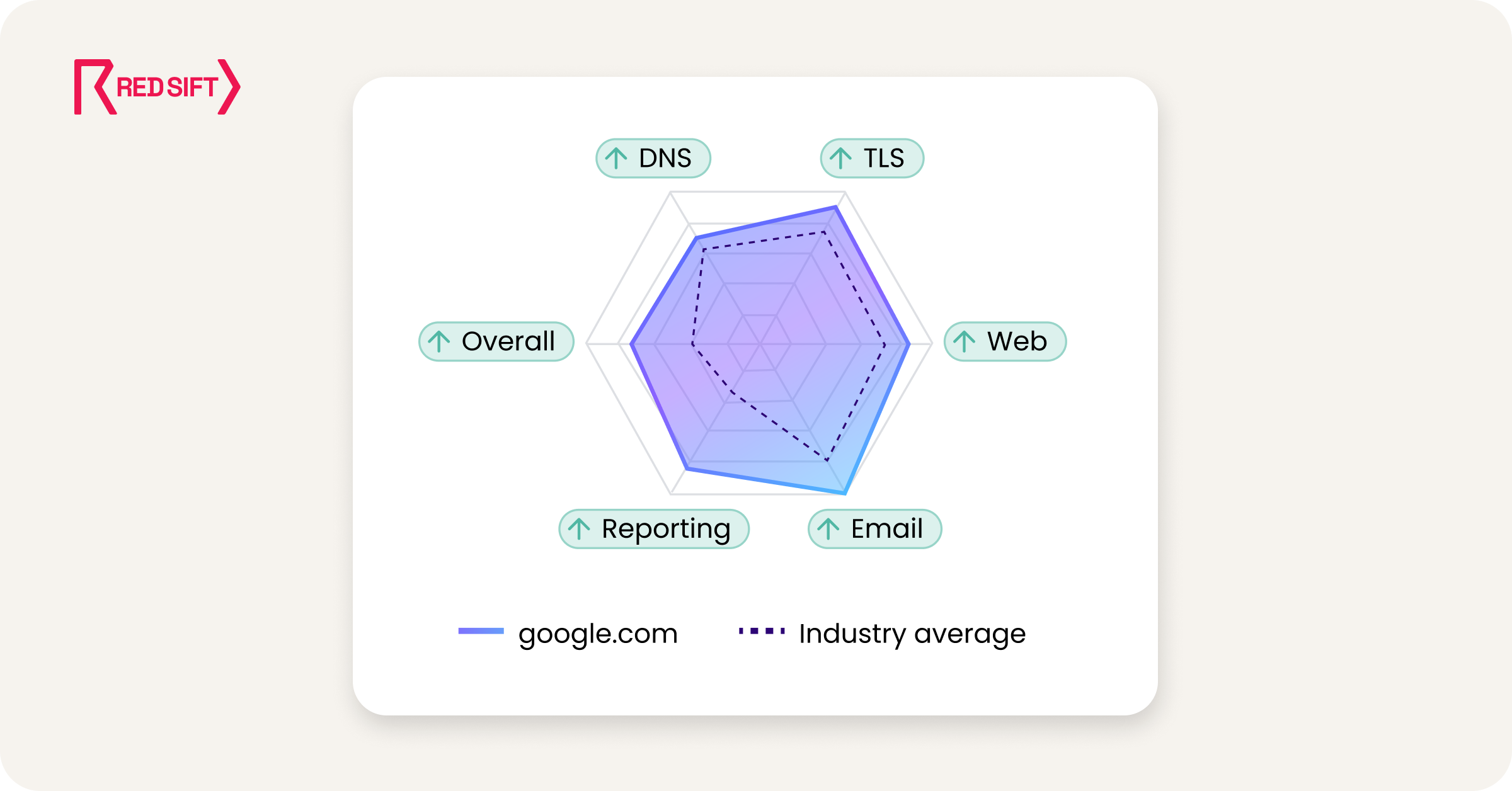

Results are presented in two layers: a clear, plain-English overview for fast understanding and decision-making, and a more detailed technical view for engineers who need configuration specifics to implement fixes.

What early testers found valuable
Early testers used Radar Lite to assess their own domains, investigate unfamiliar senders, and compare configurations across their industry. Across these use cases, a few themes consistently stood out.
- Save time with instant, actionable visibility from a single prompt. “Radar Lite is helpful for a quick overview of suspicious IP addresses, domains, or senders I’m seeing through my tenants. It’s incredibly convenient; I just type “Evaluate xyz.domain” and get an immediate answer without logging in. Anyone who wants passive reconnaissance information or is just curious about a sender could use this with great results!” Zachary Bennett, IT & Security Manager at FHC
- Prioritize confidently using real-world context and comparative insights. “Being able to compare our domain against others instantly adds context. It helps us prioritize with confidence because we can see what’s normal, what’s weak, and where we’re ahead.” Frank L. Smith III, Director of Information Security at GC Foods
- Access expert-grade analysis without needing specialist knowledge. “Radar Lite would be an excellent service for most folks below the "corporate-grade" world, e.g. ranging from hobbyists to the "IT person" at a smaller company. It would be most useful to people who run things on the internet but don’t have in-house security personnel or access to fancy consultants.” Adam Newbold, Founder at Neatnik
Radar Lite: A focused, streamlined version of Radar
Radar Lite is intentionally designed as a streamlined, purpose-built experience. Rather than exposing a general-purpose LLM, we narrowed the scope to deal exclusively with fast, reliable domain security assessments.
At its core, Radar Lite uses small, custom models to interpret domain- and protocol-specific questions and generate focused outputs. This allows us to offer the tool free to the community, while keeping it performant and predictable. Questions outside that scope, such as general-purpose queries, aren’t supported.
Radar Lite is also designed for one-off assessments rather than open-ended conversations. Each query is treated independently, ensuring results remain clear, bounded, and easy to reason about.
To keep analysis efficient and reliable at scale, we apply practical limits and optimizations. This includes restricting how many domains can be compared in a single query, aggressively caching security checks, and rate limiting network-intensive operations such as DNS lookups and certificate handshakes. These choices help us provide consistent results without placing unnecessary load on the public internet.
For teams that need deeper context, higher volumes, or true real-time analysis, Radar is built to support that level of continuous interrogation across your environment.
See it in action
Radar Lite reflects Red Sift’s belief that better security shouldn’t require specialist knowledge or complex tooling. By making domain security easier to understand and act on, Radar Lite helps teams of all sizes play their part in building a safer internet.
Visit redsift.com/radar-lite, ask a question about your domain and see how AI-powered security analysis should work.
Check your domain setup now





