
DMARC
What is DMARC?
DMARC stands for Domain-based Message Authentication, Reporting, and Conformance. It’s an outbound email security protocol that allows domain owners to take back control of their email identity by telling receiving inboxes to reject spoof emails.
DMARC stops bad actors from pretending to be you and sending phishing emails to your employees, customers, and supply chain. This authentication of an email’s origin with DMARC also greatly improves deliverability.
Why is DMARC important?
The more companies and institutions enforce a DMARC policy of p=reject for their outbound email, the safer the email ecosystem becomes overall. This is because attackers and bad actors will have fewer domains to ride on the back of to carry out attacks. So as a result, more sensitive information is protected, industry requirements are met, more money is saved and fewer attacks are successful.
What type of threats does DMARC protect against?
DMARC is an outbound security protocol, meaning it simultaneously protects recipients and your brand reputation from being exploited. It’s important to remember that bad actors who use your domain to trick people into opening emails aren’t doing so by chance, they’re piggybacking off the weight of your brand reputation and relying on it to encourage email opens.
DMARC stops this exact domain impersonation, by telling recipient servers not to accept any emails which aren’t authenticated to have come from you. So, bad actors cannot use your domain to send phishing emails and carry out Business Email Compromise (BEC).
What is the difference between reporting and enforcement?
A critical aspect of DMARC is setting the appropriate policy, defined by the "p=" tag in your DMARC record. This policy dictates how receiving mail servers should handle emails that fail DMARC authentication. The primary policy options are "p=none", “p=quarantine” and "p=reject," each serving distinct purposes in your email security strategy.
DMARC reporting (p=none)
Setting your DMARC policy to "p=none" places your domain in a monitoring state. In this mode, no action is taken on emails that fail DMARC checks; they are delivered as usual. The primary benefit of "p=none" is the generation of DMARC reports, which provide visibility into your email ecosystem. These reports help you identify legitimate and unauthorized sources sending emails on behalf of your domain. This insight is crucial for understanding your current email authentication status and planning necessary adjustments.
DMARC transition (p=quarantine)
Setting your DMARC policy to p=quarantine strikes a balance between visibility and protection by diverting emails that fail authentication to the recipient’s spam or junk folder instead of outright rejecting them. This provides a safety net, allowing organizations to mitigate email spoofing risks while minimizing the chances of accidentally blocking legitimate emails.
It also serves as a transitionary step before enforcing p=reject, giving security teams time to analyze DMARC reports, fine-tune SPF and DKIM configurations, and ensure all legitimate email sources are properly authenticated. While p=quarantine reduces the impact of fraudulent emails, it does not fully prevent them from being delivered, making it a critical but temporary phase in the path to full DMARC enforcement.
DMARC enforcement (p=reject)
Transitioning to "p=reject" enforces DMARC authentication strictly. With this policy, any email that fails DMARC validation is rejected outright by the receiving server, preventing it from reaching the recipient's inbox. This level of enforcement offers robust protection against domain spoofing and phishing attacks, as only emails that are authenticated and aligned with your domain policies are delivered. Implementing "p=reject" ensures that malicious actors cannot use your domain to send fraudulent emails.


Why reporting isn’t enough
Adopting DMARC is a phased process. Starting with "p=none" allows you to monitor email flows without disrupting legitimate communications. During this phase, analyze DMARC reports to configure SPF and DKIM records correctly for all legitimate email sources. Once confident in your email authentication setup, you can progress to enforcement policies like "p=quarantine" (which directs failing emails to the spam/junk folder) and eventually "p=reject" for full protection.
It's important to note that while "p=none" provides valuable monitoring data, it does not prevent malicious emails from being delivered. Therefore, remaining at "p=none" leaves your domain vulnerable to abuse. Achieving a "p=reject" policy is the ultimate goal for securing your domain, as it actively blocks unauthorized emails. However, this transition should be managed carefully to ensure all legitimate email sources are properly authenticated, minimizing the risk of disrupting valid communications and passing through the “p=quarantine” stage.
To fully secure your emails, "p=reject" provides stringent protection against ever-growing threats. Starting with “p=none” is an excellent start and a structured implementation plan from Red Sift, you can enhance your domain's email security posture.
What are the business benefits of implementing DMARC?
Aside from providing a strong email security posture, DMARC can offer some real business benefits too. Below are some of the key advantages of implementing DMARC.
Enjoy complete visibility
DMARC provides reports showing most, if not all, emails that come from your organization’s domain. This contrasts with traditional cybersecurity solutions which only pick up inbound phishing emails. Without DMARC, organizations are not getting a complete picture of the number and scale of attacks against them.
Protect your reputation and shut down brand abuse
Phishing attacks that use exact impersonation can cause considerable reputational damage. Phishing scams attract negative press, with liability often attributed to the organization that has been impersonated.
Ensure financial security
Paying fake invoices or completing wire transfers from emails impersonating a business’ CEO is common.
Get your registered logo on your emails
BIMI (Brand Indicators for Message Identification) is a standard that enables your registered logo to be visible in the avatar slot of any DMARC authenticated emails you send, by using Verified Mark Certificates. BIMI increases your brand impressions, and research has found it has a significant positive impact on consumer trust, interaction, and purchasing decisions. Being DMARC compliant means you’re eligible to take advantage of this brand-enhancing reward.
Improve email deliverability
When DMARC is set up correctly at a policy of p=reject, senders signal to ISPs that they are actively taking measures to authenticate their emails and improve their domain security. This builds trust with ISPs, reducing the likelihood of legitimate emails being mistakenly marked as spam or phishing attempts.
Nurture trust
Organizations that fail to take the necessary precautions to prevent email spoofing are likely to be considered less trustworthy. Customers may not trust emails that supposedly come from these organizations and could be deterred from using email to communicate with them, which can impact on those organizations’ ability to communicate effectively with their customers. By implementing DMARC, you’re putting a robust measure that confirms your organization’s identity in place
Identify and remove shadow IT
Shadow IT refers to legacy systems or technology set up by various departments in a business to plug a gap in existing infrastructure, and it’s not always easy to identify or remove. DMARC gives you the visibility necessary to identify and resolve any outlying software or systems, meaning nothing will accidentally be sent out by these legacy systems. Implementing DMARC uncovers all the email services sending emails from your domain, whether you officially know about them or not.


How DMARC supports compliance and regulation efforts
DMARC helps organizations comply with email security recommendations made by global government bodies such as NIST, NCSC, and the European Commission.
Comply with NIS2
The EU's revised Directive on Security of Network and Information Systems (NIS2 Directive) has dramatically increased the regulatory pressure on organizations to take proactive action against phishing through a DMARC policy of "reject.”
The NIS2 Directive is an EU regulation that establishes a high common level of cybersecurity across the EU. For 'Essential and Important Entities,' compliance with this directive is mandatory.
Although the text of the NIS2 Directive does not explicitly mention DMARC or a "reject" policy, several of its requirements are related to the principles that DMARC upholds, and the absence of a DMARC policy of "reject" could be considered to weaken compliance with as many as five of direct NIS2 requirements or principles.
- Security by Design and by Default
- The NIS2 Directive requires ‘providers of public electronic communications networks or of publicly available electronic communications services’ to implement security by design and by default. As a global and well-accepted internet standard for the prevention of email domain impersonation, a DMARC policy of “reject” forms an important part of a security by design and by default strategy.
- Risk Management Measures
- The NIS2 Directive requires 'Essential and Important Entities' to take appropriate and proportionate technical and organizational measures to manage the risks posed to the security of network and information systems. A DMARC "reject" policy aligns with this requirement as it is a key measure to manage the risk of email phishing and spoofing attacks, which can lead to the risks outlined in this document.
- Supply Chain Security
- The NIS2 Directive requires entities to ensure the security of their network and information systems, including those of their supply chain. A DMARC "reject" policy can help by ensuring that only authorized third-party vendors can send emails on behalf of the entity, which can help prevent phishing attacks that originate from compromised vendors as well as protect the third-party vendors themselves from becoming victims of attacks that impersonate an organization.
- Incident Reporting
- Entities must report incidents having a significant impact on the continuity of essential services. While DMARC itself is not a reporting mechanism for security incidents, the detailed aggregate and forensics reports it generates can help organizations identify and respond to security incidents related to email spoofing.
- Resilience
- Entities are required to take measures to ensure the resilience of their systems and networks. A DMARC "reject" policy contributes to this by protecting the organization's email communication system, a critical part of its network, from being misused by unauthorized senders.
Comply with Microsoft, Google and Yahoo’s bulk sender requirements
From February 2024, Microsoft, Google and Yahoo rolled out new requirements for bulk senders, ushering in a new era of email compliance, which includes DMARC implementation. Microsoft, Google and Yahoo now require bulk senders – those who send more than or around 5,000 emails daily – to meet a set of authentication measures to ensure secure email delivery to addresses ending in gmail.com or yahoo.com.
The requirements came into effect on February 1, 2024, and include:
- Set up a SPF and DKIM for each domain that sends mail
- Send with an aligned ‘From’ domain in either the SPF or DKIM domains
- Publish a DMARC policy for each domain that sends mail with a least a policy of “p=none”
- Ensure that sending domains or IPs have FcrDNS set up
- Use a TLS connect for transmitting emails
- Enable one-click unsubscribe for recipients of promotional mail
- Keep spam rates under 0.10% as reported by Google Postmaster Tools
Comply with DORA
The Digital Operational Resilience Act (DORA) is a regulatory framework by the European Union aimed at ensuring the digital operational resilience of the financial sector. It seeks to establish a stringent, harmonized set of rules for digital operational resilience, including areas such as ICT risk management, incident reporting, digital operational resilience testing, and more.
Even if an organization is not classified as a financial institution, DORA defines criticality thresholds for services provided to financial institutions. If an organization is a direct service provider to a financial institution and its services meet these thresholds, then the company is subject to DORA. Furthermore, it is likely that under DORA, these financial institutions push more stringent security controls onto their providers, including DMARC with a policy of “reject”.
While DORA does not go into specific technical detail, it does press three relevant aspects for DMARC at a policy of “reject”:
- ICT Risk Management
- One of DORA's key aspects is to ensure effective ICT risk management. Implementing a DMARC "reject" policy directly contributes to this goal by preventing phishing attacks, email spoofing, and other email-based threats. This enhances the security of the ICT ecosystem, aligning with DORA's objectives.
- Third-Party Risk
- DORA requires financial institutions to manage and mitigate risks from their third-party service providers, including communication service providers. Implementing a DMARC "reject" policy can help reduce the risk posed by email-based threats, thereby enhancing security posture and reducing third-party risk for its financial institution clients.
- Operational Resilience
- DORA places a strong emphasis on the operational resilience of financial services providers. A DMARC "reject" policy can help enhance operational resilience by ensuring the integrity and authenticity of email communications, reducing the risk of disruptive incidents caused by phishing or other email-based attacks.
Comply with PCI 4.0.1
The Payment Card Industry Data Security Standard (PCI DSS) is a globally recognized framework designed to ensure that all companies that accept, process, store, or transmit credit card information maintain a secure environment. Implementing DMARC is recognised as an essential part of meeting these requirements. By ensuring that emails sent from a domain are authenticated through SPF and DKIM protocols, and providing domain owners with visibility into unauthorized use of their domain, DMARC supports PCI DSS 4.0.1's goal of protecting cardholder data environments. It reduces the risk of phishing attempts that could lead to breaches, helping organizations establish trust and improve security postures.
PCI DSS 4.0.1 calls for organisations to adopt a proactive, risk-based approach to cybersecurity, and DMARC aligns seamlessly with this framework. By enabling domain owners to enforce a "reject" policy for unauthenticated emails, DMARC actively prevents malicious emails from reaching their targets, addressing key compliance requirements around risk mitigation. Reporting capabilities also provide valuable insights into email ecosystems, enabling organizations to identify vulnerabilities and ensure continuous improvement. As a critical layer in email security, DMARC not only strengthens compliance with PCI DSS 4.0 but also enhances overall organisational resilience against evolving cyber threats.
To prepare for PCI DSS 4.0.1 compliance by March 31, 2025, organizations should start by conducting a gap analysis to identify areas that need improvement. Prioritizing the implementation of automated certificate management tools can help manage the complexities of certificate validation and renewal, such as Red Sift Certificates. Additionally, businesses should engage with Qualified Security Assessors (QSAs) to ensure their compliance strategies are sound and effective.
Comply with GDPR
General Data Protection Regulation (GDPR) came into force in May 2018, requiring you to have Data Processing Agreements (DPAs) with every cloud service provider that handles EU consumer data on your behalf. With DMARC, if a cloud service provider does send emails using your company’s domain name in the ‘From’ field, then DMARC will reveal them to you. While a DMARC "reject" policy is not explicitly required by GDPR.
Who is DMARC supported by?
DMARC has been widely adopted by most email receivers (including Google, Yahoo, and Microsoft), which means that most consumer inboxes are already protected.
In addition, since February 2024, Google and Yahoo have introduced new email requirements for bulk senders (those who send more than 5,000 emails a day). On April 2025, Microsoft has also introduced new email requirements for bulk senders. These requirements stipulate that you:
- Send from a domain with a DMARC policy of at least p=none
- Set up one-click unsubscribe for recipients of promotional mail
- Keep spam rates under 0.10%
Those who fail to meet these requirements will see Microsoft, Google and Yahoo limiting sending rates or marking legitimate messages as spam. To find out more, visit our informational Microsoft, Google and Yahoo page.
How DMARC works
DMARC works using the existing security protocols SPF and DKIM. Your SPF record is a whitelist of IP addresses you’ve authorized to send emails using your domain. DKIM acts like a digital signature, letting the recipient know you are who you say you are. When you first configure DMARC, you’ll spend some time classifying which senders you’ve authorized to send emails using your domain, and which you haven’t.
Both SPF and DKIM are essential to your email security setup, but neither prevents exact impersonation. While the protocols tell the recipient who the email is from, the recipient has no instruction to act on this knowledge, i.e. it doesn’t know what to do with your email.
So, DMARC works by combining the results of SPF and DKIM to determine if your email is authentic and authorized. Then, the DMARC policy you have in place tells recipient servers what to do with it.
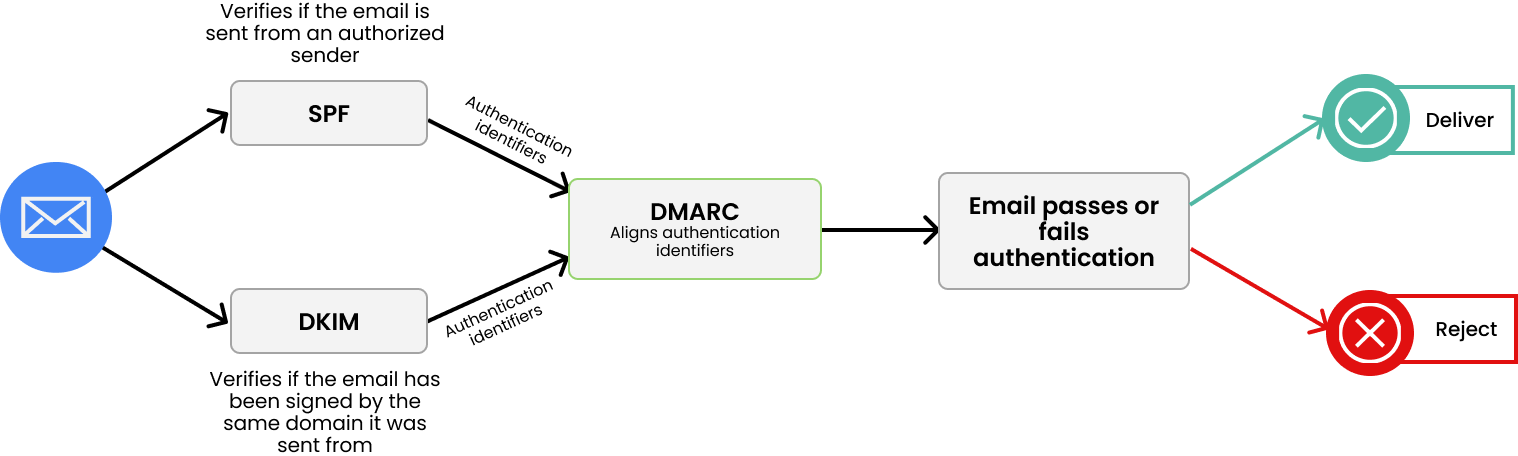

The 3 types of DMARC policies
Your DMARC policy is essentially the instruction you give to receiving servers, telling them what to do with emails that come from your domain. There are three policies to choose from:
- p=none: this policy tells the recipient server to accept all emails from your domain, regardless of whether they pass authentication or not.
- p=quarantine: this policy tells the recipient server to send any emails from your domain that fail authentication to spam.
- p=reject: this policy tells the recipient server to reject any emails coming from your domain that fail authentication.


Typically, when you implement DMARC for the first time you will start with a policy of p=none. This policy means that you are in reporting-only mode and you don't want any policy to be applied to your emails if they fail DMARC. During this stage you are simply gaining visibility into how your domain is being used around the world and what services are sending emails on your behalf. At this stage you simply identify your legitimate sending services and configure each one with SPF and DKIM so that they send DMARC compliant emails.
Once you are confident that your sending services are fully configured you can change your DMARC policy from p=none; to p=quarantine. This means that from this point on any emails that fail DMARC will have this policy applied to them, which means that usually they will be sent to the spam folder of the recipient.
If you do not encounter any issues during the p=quarantine; stage and only spoofing emails are being quarantined you can change the policy once more from p=quarantine to p=reject. At p=reject, you are telling recipients to reject any emails that fail DMARC. This means that end recipients will never receive the emails as they will simply be rejected at the SMTP level. This is the strongest level of protection which means that no one will be able to spoof your domain. Any emails that do not originate from your legitimate sending services will be rejected as they will fail DMARC.
To learn more about the technical ins and outs of DMARC, visit our dedicated DMARC chapter in our Technical Configuration Guide.


