Der beste Leitfaden zur E-Mail-Sicherheit für Cybersicherheitsverantwortliche

- SPF und DKIM
- Was ist das Sender Policy Framework (SPF)?
- Wie funktioniert SPF?
- Was ist eine SPF-Abfrage?
- Was ist ein SPF-include?
- Was ist das SPF-Query-Limit?
- Wie umgehe ich das SPF-Query-Limit?
- Warum schlägt mein SPF-Eintrag fehl?
- Was ist DomainKeys Identified Mail (DKIM)?
- Wie funktioniert DKIM?
- Was ist eine DKIM-Signatur?
- Was ist ein DKIM-Schlüssel?
- Ist DKIM für die E-Mail-Sicherheit unverzichtbar?
- Was ist der Unterschied zwischen SPF und DKIM?
- SPF und DKIM
- Was ist das Sender Policy Framework (SPF)?
- Wie funktioniert SPF?
- Was ist eine SPF-Abfrage?
- Was ist ein SPF-include?
- Was ist das SPF-Query-Limit?
- Wie umgehe ich das SPF-Query-Limit?
- Warum schlägt mein SPF-Eintrag fehl?
- Was ist DomainKeys Identified Mail (DKIM)?
- Wie funktioniert DKIM?
- Was ist eine DKIM-Signatur?
- Was ist ein DKIM-Schlüssel?
- Ist DKIM für die E-Mail-Sicherheit unverzichtbar?
- Was ist der Unterschied zwischen SPF und DKIM?
SPF und DKIM
Was ist das Sender Policy Framework (SPF)?
Das Sender Policy Framework (SPF) ist ein E-Mail-Authentifizierungsprotokoll, das verhindern soll, dass Angreifer E-Mails versenden, die scheinbar von Ihrer Domain stammen. Eine SPF-Richtlinie gibt empfangenden Mailservern an, welche Absenderquellen für Ihre Domain legitim sind, und hilft so, Identitätsdiebstahl, Phishing und Domain-Imitation zu verhindern. Seit 2026 ist SPF eine grundlegende Voraussetzung für Organisationen, die Massen-E-Mails versenden.
Wie funktioniert SPF?
Ihre SPF-Richtlinie wird in Ihrem Domain Name System (DNS) als TXT-Eintrag veröffentlicht und listet die Mailserver (IP-Adressen) auf, die berechtigt sind, E-Mails in Ihrem Namen zu versenden. Wenn eine E-Mail verschickt wird, prüft der empfangende Mailserver diese Richtlinie, um zu bestätigen, ob die sendende IP-Adresse erlaubt ist. Ist dies der Fall, wird die Nachricht zugestellt; andernfalls kann sie als Spam markiert oder abgelehnt werden.
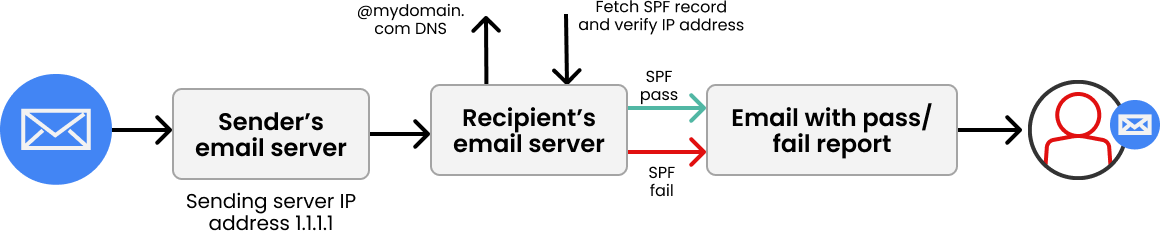

Was ist eine SPF-Abfrage?
Eine SPF-Abfrage (Lookup) bezeichnet den Vorgang, bei dem das empfangende DNS die im include-Befehl Ihres Eintrags aufgeführten IP-Adressen „nachschlagen“ muss, um zu überprüfen, ob sie mit der IP-Adresse übereinstimmen, von der Ihre E-Mail gesendet wird.
Was ist ein SPF-include?
Ein SPF-include ist ein Mechanismus in SPF-Einträgen, durch den Domaininhaber die SPF-Einträge anderer Domains in ihre eigene SPF-Policy aufnehmen können. Das erleichtert die Verwaltung und berücksichtigt die Versandrichtlinien der inkludierten Domains bei der Validierung von E-Mails, die von der Hauptdomain verschickt werden.
Was ist das SPF-Query-Limit?
Das SPF-Query-Limit entspricht der maximalen Anzahl von Anfragen, die ein empfangendes DNS für eine Domain ausführen darf. Diese ist auf 10 festgelegt.
Sie können eine unbegrenzte Anzahl an Einzel-IP-Adressen in Ihren Eintrag aufnehmen, ohne zusätzliche DNS-Abfragen zu erzeugen, da diese direkt im Eintrag ersichtlich sind.
Das gilt jedoch nicht für include-Anweisungen, bei denen jede darin enthaltene IP-Adresse eine zusätzliche Abfrage beim empfangenden DNS bedeutet. Das zählt alles zur maximalen Obergrenze von 10.
Zum Beispiel können Sie 3 IP-Adressen direkt in Ihrem SPF-Eintrag angeben, einen include-Befehl für Google (mit 4 IP-Adressen) und einen für Mimecast (mit 6 IP-Adressen). Für die direkt sichtbaren IPs sind keine Abfragen nötig, für die includes von Google und Mimecast jedoch schon. In diesem Fall kommen Sie auf das Maximum von 10 Abfragen.
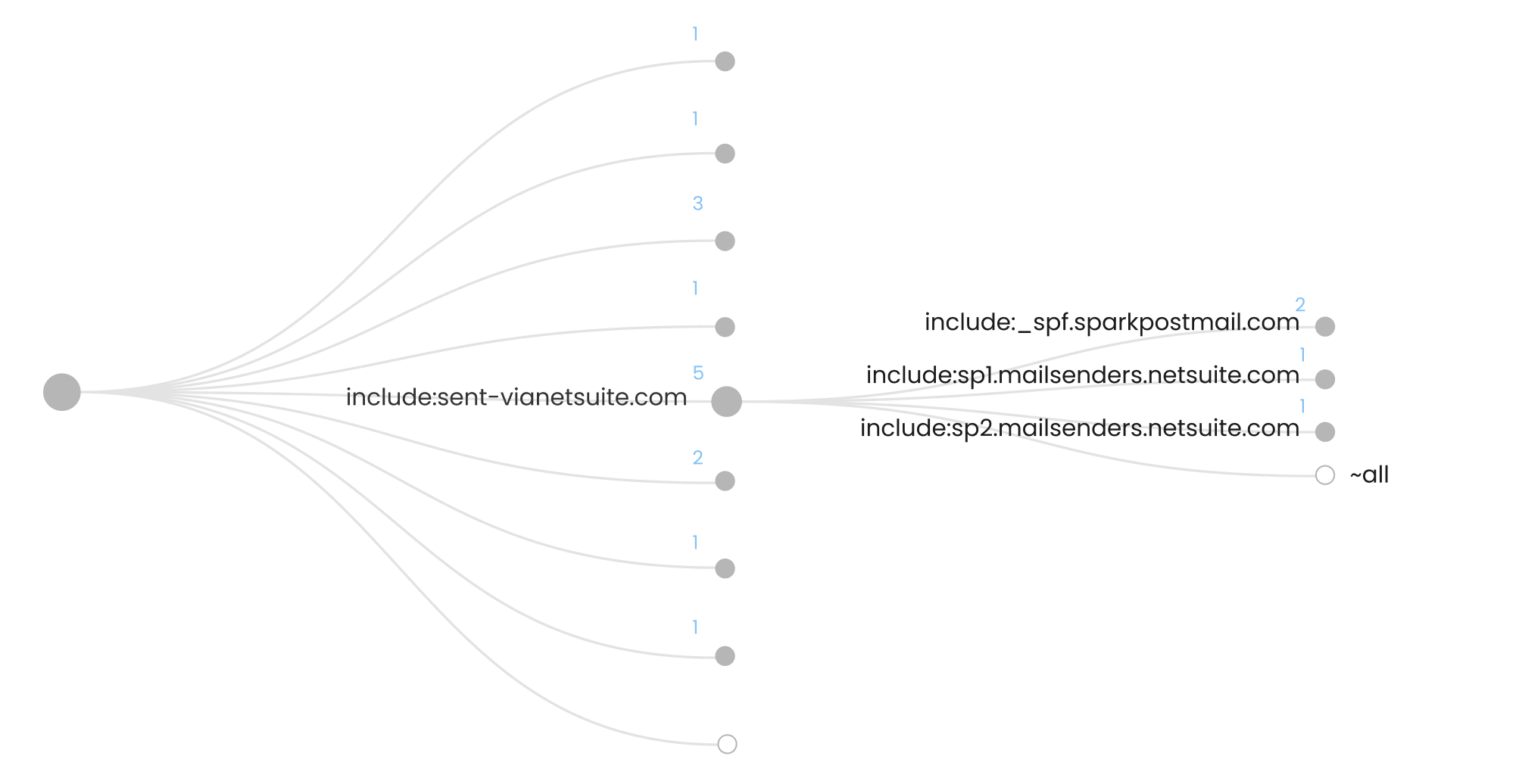

Wie umgehe ich das SPF-Query-Limit?
In Wirklichkeit reichen 10 Abfragen nicht aus, weil die meisten Unternehmen mehrere Tools nutzen, die E-Mails für sie versenden. Jedes hat seinen eigenen include-Befehl, der wiederum IP-Adressen enthält und somit weitere Abfragen benötigt. Überschreiten Sie das Limit, wird die Authentifizierung wahrscheinlich fehlschlagen und Ihre Zustellrate leidet. Seit 2026 gelten dynamische SPF-Lösungen als empfohlener Weg zur Handhabung dieser Begrenzung, da sie die manuelle Pflege und das ständige Flattening von SPF-Einträgen ersetzen.
Warum schlägt mein SPF-Eintrag fehl?
Ein Hauptgrund dafür, dass der SPF-Eintrag für Ihren E-Mail-Verkehr fehlschlägt, ist die Fehlermeldung „zu viele DNS-Abfragen“. Die SPF-Spezifikation begrenzt die Anzahl der DNS-Anfragen auf maximal 10. Erzeugt Ihr SPF-Eintrag mehr als 10 Abfragen, schlägt SPF fehl. Zu den SPF-Mechanismen, die für DNS-Abfragen zählen, gehören: a, ptr, mx, include, redirect und exists. Die Mechanismen „ip4“, „ip6“ und „all“ zählen nicht zu diesem Limit.
Falls Ihnen das alles zu technisch erscheint, hier ein Beispiel: G Suite allein beansprucht vier DNS-Abfragen, Hubspot für Marketing weitere sieben – und schon sind Sie über dem Limit von 10! Sobald Sie die Schwelle überschreiten, besteht das Risiko, dass Ihre E-Mails gelegentlich bei der Überprüfung scheitern. Deshalb setzen Organisationen ab 2026 auf dynamisches SPF-Management anstatt E-Mail-Einträge händisch zu pflegen und zu flatten.
Was ist DomainKeys Identified Mail (DKIM)?
DKIM steht für DomainKeys Identified Mail und ist ein E-Mail-Authentifizierungsprotokoll, das verhindern soll, dass E-Mails während der Übertragung verändert werden – eine Methode, die oft bei Phishing und Betrugsversuchen eingesetzt wird.
Wie funktioniert DKIM?
DKIM ist eine neuere und komplexere Norm als SPF. Es basiert auf asymmetrischer Kryptografie, um bestimmte Teile der E-Mail zu signieren. Der private Schlüssel liegt sicher auf dem sendenden Server und ist für den Endnutzer nicht einsehbar. Der öffentliche Schlüssel wird im DNS der Absenderdomain veröffentlicht, um die E-Mail-Signatur zu verifizieren.
Praktisch bedeutet das: Bei Erstellung einer E-Mail werden Header und Inhalt mit dem privaten Schlüssel des Absenders signiert. Diese digitale Signatur wird dann im Header der Nachricht mitgesendet. Beim Empfang (wenn DKIM aktiviert ist) ruft der empfangende Server den öffentlichen Schlüssel ab und prüft, ob die E-Mail tatsächlich vom Absender signiert wurde. Bei erfolgreicher Prüfung ist nachgewiesen, dass die Absenderdomain wirklich der Ursprung der Nachricht ist und dass Header sowie Inhalt während der Übertragung nicht verändert wurden.
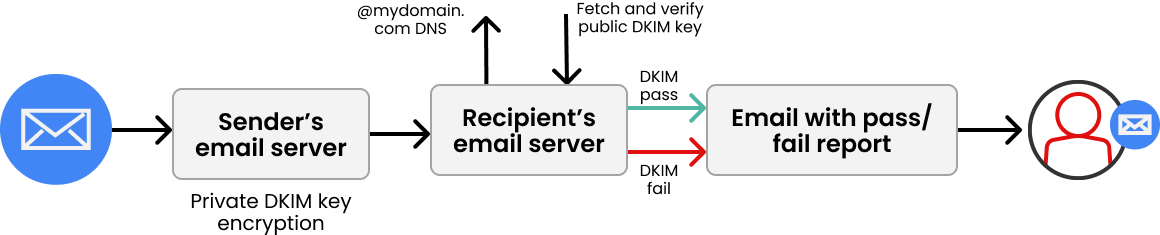

Was ist eine DKIM-Signatur?
Eine DKIM-Signatur ist ein eindeutiger kryptografischer Wert, der im Header einer ausgehenden E-Mail integriert ist. Er wird basierend auf dem privaten DKIM-Schlüssel des Absenders generiert und ermöglicht es dem empfangenden Server, den zugehörigen öffentlichen Schlüssel im DNS abzurufen und so zu bestätigen, dass die Nachricht aus einer autorisierten Quelle stammt und ihr Inhalt während des Transports nicht verändert wurde.
Was ist ein DKIM-Schlüssel?
Ein DKIM-Schlüssel besteht aus einem Schlüsselpaar für die DKIM-Authentifizierung. Der private Schlüssel wird sicher auf dem Server des absendenden Mailservers gespeichert und erzeugt die DKIM-Signatur jeder ausgehenden E-Mail. Der öffentliche Schlüssel wird als TXT-Eintrag im DNS der Absenderdomain veröffentlicht, sodass empfangende Server die Signatur überprüfen und die Integrität sowie Authentizität der E-Mail sicherstellen können.
Alle technischen Details zu DKIM finden Sie in unserem technischen Einrichtungsleitfaden.
Ist DKIM für die E-Mail-Sicherheit unverzichtbar?
Ja. DKIM (DomainKeys Identified Mail) ist ein wesentliches Authentifizierungsprotokoll für E-Mails, das gegen Spoofing, Phishing und Manipulation von Nachrichten schützt. Es fügt jeder ausgehenden E-Mail eine kryptographische Signatur hinzu, mit der empfangende Server prüfen können, ob der Inhalt unverändert und die E-Mail von einer autorisierten Domain stammt. Ebenso ist DKIM ein zentraler Bestandteil der DMARC-Überprüfung und arbeitet mit SPF zusammen, um das Domain-Alignment sicherzustellen und die E-Mail-Sicherheit zu erhöhen. Die wichtigsten E-Mail-Anbieter fordern DKIM inzwischen obligatorisch für Massenmails – somit ist es im Jahr 2026 unverzichtbar für die Zustellbarkeit.
Was ist der Unterschied zwischen SPF und DKIM?
SPF (Sender Policy Framework) überprüft, ob eine E-Mail von einer IP-Adresse stammt, die im SPF-Eintrag der Absenderdomain autorisiert ist. DKIM (DomainKeys Identified Mail) verwendet eine kryptografische Signatur, die über einen öffentlichen Schlüssel im DNS überprüft werden kann, um zu garantieren, dass der Nachrichteninhalt nicht verändert wurde und die E-Mail von einer berechtigten Domain stammt. SPF konzentriert sich auf die Absendeberechtigung, während DKIM die Integrität und Authentizität der Nachricht sicherstellt.


Häufig gestellte Fragen: Leitfaden zur E-Mail-Sicherheit
Alle Maßnahmen zur E-Mail-Sicherheit (außer DMARC) sind wirkungslos, wenn eine bösartige E-Mail scheinbar von einer legitimen Domain stammt. Grund dafür ist ein Fehler im Simple Mail Transfer Protocol (SMTP). Im Oktober 2008 hat die Network Working Group dieses offiziell als 'grundsätzlich unsicher' eingestuft und festgestellt, dass jeder eine Domain imitieren und betrügerische E-Mails im Namen des Domaininhabers versenden kann.
Jeder mit sehr grundlegenden Programmierkenntnissen kann sich das nötige Wissen zur Imitation der E-Mail-Identität einer anderen Person durch eine schnelle Google-Suche aneignen. Das Ergebnis ist eine E-Mail, die legitim aussieht und keine typischen Phishing-Anzeichen aufweist. Bei 3,4 Milliarden Phishing-E-Mails täglich bleiben E-Mail-Systeme das Hauptziel von Cyberkriminellen.
SPF (Sender Policy Framework) prüft, ob eine E-Mail von einer durch den SPF-Eintrag der Absenderdomain autorisierten IP-Adresse versendet wurde. Dies geschieht über einen DNS-TXT-Eintrag mit der Liste der autorisierten Mailserver.
DKIM (DomainKeys Identified Mail) nutzt eine kryptografische Signatur, die über einen öffentlichen Schlüssel im DNS validiert wird, um zu bestätigen, dass der Inhalt der E-Mail nicht verändert wurde und von einer autorisierten Domain stammt. Beide sind essenziell für die E-Mail-Sicherheit, verhindern aber keine exakte Imitation.
Obwohl diese Protokolle dem Empfänger zeigen, von wem die E-Mail stammt, erhält der Empfänger keine Anweisung, wie er darauf reagieren soll. Große Postfachanbieter verlangen ab 2026 SPF und DKIM für den Versand von Massennachrichten.
DMARC steht für Domain-based Message Authentication, Reporting und Conformance. Es ist ein Protokoll für ausgehende E-Mail-Sicherheit, mit dem Domaininhaber empfangenden Postfächern mitteilen können, dass gefälschte E-Mails abgelehnt werden sollen. DMARC kombiniert die Ergebnisse von SPF und DKIM, um festzustellen, ob Ihre E-Mail legitim und autorisiert ist.
Die DMARC-Richtlinie (definiert durch den "p="-Tag im DNS-Eintrag) gibt daraufhin den empfangenden Servern vor, wie mit solchen E-Mails zu verfahren ist. DMARC verhindert exakte Domain-Imitation, indem es empfangenden Servern anweist, keine E-Mails zu akzeptieren, die nicht authentifiziert sind. 2026 ist DMARC für Organisationen, die Massen-E-Mails versenden, zum Standard geworden.
Die SPF-Spezifikation begrenzt DNS-Lookups auf 10. Überschreitet Ihr SPF-Eintrag diesen Wert, schlägt die SPF-Prüfung fehl. Zu den gezählten Mechanismen gehören: a, ptr, mx, include, redirect und exists. In der Praxis reichen 10 Lookups meist nicht aus, da viele Unternehmen mehrere E-Mail-Versandtools nutzen.
G Suite allein belegt 4 DNS-Lookups, dazu kommen beispielsweise 7 Lookups für Marketing mit HubSpot – und schon ist das Limit überschritten. Sobald Sie mehr als 10 SPF-Lookups haben, kommt es zu zufälligen Fehlern bei der E-Mail-Validierung. Daher setzen Unternehmen im Jahr 2026 auf dynamisches SPF-Management, anstatt zu versuchen, abgeflachte Einträge manuell zu pflegen.
Mail Transfer Agent Strict Transport Security (MTA-STS) ist ein Standard, der die Verschlüsselung von E-Mails beim Versand zwischen zwei Mailservern ermöglicht. Er legt fest, dass E-Mails nur über eine mit Transport Layer Security (TLS) verschlüsselte Verbindung gesendet werden dürfen, was eine Abfangbarkeit durch Cyberkriminelle verhindert. SMTP allein bietet keine Sicherheit und ist daher anfällig für Man-in-the-Middle-Angriffe, bei denen Kommunikation abgefangen und ggf. verändert wird.
Darüber hinaus ist Verschlüsselung in SMTP optional, sodass E-Mails im Klartext übertragen werden können. Ohne MTA-STS kann ein Angreifer die Kommunikation abfangen und erzwingen, dass die Nachricht im Klartext übertragen wird. 2026 ist MTA-STS eine Standard-Sicherheitsmaßnahme für Organisationen mit sensibler Kommunikation.
Durch die Implementierung von DMARC profitieren Sie von der Blockierung von Phishing-Versuchen, die scheinbar von Ihrer Domain ausgehen, stärkerem Kundenvertrauen, reduziertem Cyberrisiko und der Einhaltung der Anforderungen für Massenaussendungen von Google, Yahoo und Microsoft.
DMARC stärkt zudem die Einhaltung von PCI DSS 4.0 und erhöht die allgemeine organisatorische Widerstandsfähigkeit gegen sich wandelnde Cyberbedrohungen. Ist die Policy auf p=reject (Durchsetzung) gesetzt, blockiert DMARC Lieferantenbetrug, Kontoübernahmen und E-Mail-Spoofing, indem es verhindert, dass Dritte Ihre Domain für Phishing-E-Mails und Business Email Compromise (BEC) nutzen. Laut dem Data Breach Investigations Report von Verizon 2025 machen BEC-Angriffe mehr als 17–22% aller Social-Engineering-Vorfälle aus.
Red Sift OnDMARC beschleunigt die DMARC-Umsetzung mit automatisierter Sendersuche, konkreten Lösungsvorschlägen, Anomalie-Erkennung und rollenbasiertem Zugriff für globale Teams. Im Jahr 2026 ermöglichen führende Plattformen es Unternehmen, p=reject-Durchsetzung innerhalb von 6–8 Wochen statt der früher üblichen sechs Monate zu erreichen.
Einer der am häufigsten genannten Vorteile von OnDMARC ist die durchschnittliche Zeit von 6–8 Wochen bis zur vollen Durchsetzung. Die leistungsstarke Automatisierung der Plattform analysiert kontinuierlich sämtliche Vorgänge auf Ihrer Domain und zeigt Hinweise und Empfehlungen für notwendige Änderungen an. Bereits 24 Stunden nach Hinzufügen Ihres individuellen DMARC-Eintrags zu DNS beginnt OnDMARC, DMARC-Berichte zu analysieren und übersichtlich in Dashboards anzuzeigen.
Große E-Mail-Anbieter wie Microsoft, Google und Yahoo verlangen ab 2024–2025 DMARC für Versender von Massennachrichten (Organisationen, die mehr als 5.000 E-Mails pro Tag versenden), und diese Anforderungen sind 2026 zum Standard geworden.
Neben den Vorgaben der Postfachanbieter setzen auch einzelne Branchen und Behördenregulierungen zunehmend auf DMARC. US-Bundesbehörden müssen DMARC verwenden, ebenso wie durch DORA regulierte Zahlungsdienstleister. Darüber hinaus stärkt die DMARC-Implementierung die Einhaltung von Vorschriften wie PCI DSS 4.0, DSGVO und NIS2. Für Cybersecurity-, E-Mail-Sicherheits- und IT-Teams ist es entscheidend, die E-Mail-Sicherheit der eigenen Organisation internationalen Best Practices und Anforderungen anzupassen.





